Tuesday, 13 December 2011
Adding Static ARP Entry In ARP Table To Prevent ARP Spoofing Attacks
Since my hostel network is a switched network, there has been number of attempts of ARP spoofing attacks so I thought to share this small tip to prevent possible ARP spoofing attacks. Adding static ARP entry of the main server in your PC would possibly prevent RP spoofing attacks however I would warn you that some people have been saying that this is not still foolproof method. Theoretically I feel adding static ARP entries in the ARP table is the ultimate solution to prevent ARP spoofing and poisoning attacks.
Linux
Anyway, in linux its pretty straight-forward and the following command would add new static ARP entry:
Replace the IP_Addr and MAC_Addr fields with the necessary IP address and MAC address. For example, to add static ARP entry of my local gateway with IP 192.168.0.1 and MAC 00:14:d1:10:ea:1c, I would do:
To view all the entries in your system's ARP table, type the following command:
And you should see one of the entries similar to kubh-gateway.local (192.168.0.1) at 00:14:d1:10:ea:1c [ether] PERM on eth0.
Windows
Similar command as discussed above should work in Windows XP, however Windows 7 gave some problem while using the above command. I had a test on how to do that and I'm posting the series of screenshots on how to make static ARP entry in windows 7. Btw, I'm sorry that I'm not windows user and hence can't give much details.
arp -a output at beginning
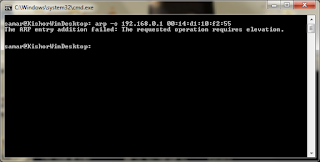
arp -s failure due to lack of privilege
Running command prompt as admin
Adding static ARP entry
arp -a final output
Please go through the given screenshots to understand the steps done while adding static ARP entries in windows 7.
Linux
Anyway, in linux its pretty straight-forward and the following command would add new static ARP entry:
sudo arp -s IP_Addr MAC_Addr
Replace the IP_Addr and MAC_Addr fields with the necessary IP address and MAC address. For example, to add static ARP entry of my local gateway with IP 192.168.0.1 and MAC 00:14:d1:10:ea:1c, I would do:
sudo arp -s 192.168.0.1 00:14:d1:10:ea:1c
To view all the entries in your system's ARP table, type the following command:
arp -a
And you should see one of the entries similar to kubh-gateway.local (192.168.0.1) at 00:14:d1:10:ea:1c [ether] PERM on eth0.
Windows
Similar command as discussed above should work in Windows XP, however Windows 7 gave some problem while using the above command. I had a test on how to do that and I'm posting the series of screenshots on how to make static ARP entry in windows 7. Btw, I'm sorry that I'm not windows user and hence can't give much details.
arp -a output at beginning
arp -s failure due to lack of privilege
Running command prompt as admin
Adding static ARP entry
arp -a final output
Please go through the given screenshots to understand the steps done while adding static ARP entries in windows 7.
Labels:
arp spoofing,
arp spoofing prevention,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Adding Static ARP Entry In ARP Table To Prevent ARP Spoofing Attacks
2011-12-13T01:32:00+05:45
Cool Samar
arp spoofing|arp spoofing prevention|security|
Subscribe to:
Post Comments (Atom)