Saturday, 7 December 2013
MyISAM to InnoDB Engine Conversion
mysql -u <user> -p -e "SELECT concat('ALTER TABLE \`',TABLE_SCHEMA,'\`.\`',TABLE_NAME,'\` ENGINE=InnoDB;') FROM Information_schema.TABLES WHERE TABLE_SCHEMA in ('database1', 'database2', 'databaseN') AND ENGINE = 'MyISAM' AND TABLE_TYPE='BASE TABLE'" | tail -n+2 > alter.sql
Once the SQL script is generated, all you need to do is run the sql file to your database server.
Note that while InnoDB is generally the better engine than MyISAM and MySQL has InnoDB as default engine since 5.5, MyISAM has its own benefits and you should make performance analysis in preferably a test environment while converting the engine type.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday, 18 November 2013
Install HTTrack On CentOS
$ wget http://download.httrack.com/cserv.php3?File=httrack.tar.gz -O httrack.tar.gz
$ tar xvfz httrack.tar.gz
$ cd httrack-3.47.27
$ ./configure
$ make && sudo make install
This should do all. If you wish not to install zlib compression support, you can skip the first step and run the configure as ./configure --without-zlib. I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday, 10 November 2013
JPEG To PDF With Imagemagick
First make sure imagemagick suite is installed in your system.
Ubuntu/Debian
CentOS/Fedora
Below are some of the examples of using convert which is a part of ImageMagick to convert Jpeg to PDF.
Single Image
Multiple Images
Resize and Convert
Negate and Convert
You can actually use different available switches to get your output as expected. I usually use PdfTk in conjunction with this technique to work in different scenarios and it really works great. I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 9 November 2013
Fix Your Ubuntu
FixUbuntu.com
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 6 November 2013
Recursion and Memoization - A Fibonacci Example
Straight from Wikipedia, memoization is an optimization technique used primarily to speed up computer programs by having function calls avoid repeating the calculation of results for previously processed inputs.
Basically, we maintain a lookup table and store the computer values for particular cases which lets us query and use the corresponding value for particular case present in the lookup tables. This reduces function call overheads. Now in order to understand why this is a great optimization technique in recursion, lets first draw a recursion tree for finding nth term in fibonacci sequence.
fib(5)
/\
/ \
/ \
/ \
fib(4) fib(3)
/\ /\
/ \ / \
/ \ / \
/ \ / \
fib(3) fib(2) fib(2) fib(1) -> 1
/\ /\ /\
/ \ / \ / \
/ \ / \ / \
/ \ / \ / \
fib(2) fib(1) fib(1) fib(0) fib(1) fib(0) -> 0
/\ | | | | |
/ \ 1 1 0 1 0
fib(1) fib(0)
| |
1 0
We can clearly see the calls to fib() with same arguments several times. For example, fib(1) is called 5 times and fib(2) 3 times. Thus, we are repeating same calculations multiple times and imagine how this would look like for large value of n. If we would have maintained the value of fib(n) in the lookup table when computed the value for the first time.
The python code without memoization looks like below and notice the runtime:
#!/usr/bin/python
def fib(n):
if n == 0:
return 0
if n == 1:
return 1
val = fib(n-1) + fib(n-2)
return val
print fib(50)
And, now with the memoization, you will notice significant improvement in runtime.
#!/usr/bin/python
known = {0:0, 1:1}
def fib(n):
if n in known:
return known[n]
known[n] = fib(n-1) + fib(n-2)
return known[n]
print fib(50)
If you run and compare above two codes, you will find that the addition of memoization significantly improves the performance of recursive functions. Recursion are generally known to be terribly slow however memoization can make the difference insignificant. Some languages now provide memoization as the language feature natively or via third party APIs such as groovy memoize.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 18 October 2013
Pattern Based Database GRANT In MySQL
We let different teams work on replicas of same database and hence append the terms such as _dev and _qa as the database prefix. And, we define GRANTS based on these patterns. An example would be something like below:
GRANT ALL ON `%\_dev`.* TO 'user'@'%' IDENTIFIED BY 'password' WITH GRANT OPTION;
I hope this proves useful for some of you guys :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 17 October 2013
How I am Trying To Keep My Eyes Safe On Computer
The problem with computer addicts is not getting their eyes off the computer for much longer period and though I've been trying to remember to keep my eyes off the computer in regular interval, I usually never implement this.
My two principles based on my readings on different websites are:
- 20-20-20: In the 20 minutes interval, keep your eyes away for 20 seconds (& view other objects which are around 20 feet away)
- 2 hrs rule: In the 2 hours interval, stay away from computers for at least 2 minutes.
But, you can not really follow the rules so easily and I had to find some other alternative to do so. This is how I am doing it now.
Create two cron jobs for each of the above mentioned methods such that notify-send is triggered in each 20 minutes and each 2 hours informing you to keep yourself safe from computers. So my /etc/crontab looked like this:
*/20 * * * * techgaun export DISPLAY=:0.0 && /usr/bin/notify-send -i /home/techgaun/Samar/scripts/eye_inv.ico "20 - 20 - 20" "Time to take rest. Keep your eye safe :)" 01 */2 * * * techgaun export DISPLAY=:0.0 && /usr/bin/notify-send -i /home/techgaun/Samar/scripts/eye_inv.ico "2 hrs eye rest" "Time to take rest for 2 minutes. Keep your eye safe :)"
You need to replace techgaun with your username and need to give correct path to the ico file if you like to use icon like me. Otherwise, you could just omit the icon in notify-send command. I hope this proves useful for some of you :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday, 16 September 2013
Two Ways To Print Lines From File Reversely
Imagine a file somefile.txt with content something like this:
b
c
d
e
Method 1:
e
d
c
b
a
Method 2:
e
d
c
b
a
You can achieve the same effect through other techniques as well but I'll stick to these simple ones :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 7 August 2013
Compile 32 Bit Binaries On 64 Bit Machine
First make sure the necessary x86 libraries are installed. We require 32-bit shared libraries for AMD64 to compile binaries in 32 bit format. The command below installs the i386 version of libc6-dev:
Now you can compile your code in 32 bit binary format using the -m32 flag where 32 represents the x86 processor (-m64 would mean x64 processor).
I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Pointers Without Pointer Variables
The code example below uses an unsigned integer variable in order to store memory addresses to point the integer array.
#includeint main(int argc, char **argv) { int num[] = {1, 2, 3, 4, 5}; unsigned int ptr; int i; ptr = (unsigned int) num; for (i = 0; i < 5; i++) { printf("%p - %d\n\n", (void *) ptr, *(int *)(ptr)); ptr = ptr + 4; } return 0; }
The same concept can be used to use non-pointer variable for pointing other datatypes. After all, its about correct type-casting and since 4 bytes datatype can hold memory addresses, pointer is not always necessary. It must be noted that the increment would be different for different datatypes. Since integer requires 4 bytes, ptr is incremented in this example. If we had character array, then ptr would have to be increased by 1 since char type requires 1 byte.
However, pointers are there to make our life easy. It was just for fun :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 28 June 2013
Rename MySQL root User [How To]
Login to the MySQL console and then type the following SQL statements:
mysql> update user set user="some_other_user" where user="root";
mysql> flush privileges;
It is often good idea to drop anonymous users and the test database because of security reasons. I bet you are never going to use that test database so why keep it? Run the SQL statements as below to do so:
mysql> drop database test;
Also, make sure you use strong passwords. You can use mysqladmin to change passwords.
The later two commands are to ensure that no log of any of your MySQL queries or admin level commands have been stored in the history.
I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 27 June 2013
Manual Sun Java Installation In Linux
Though the process was done on CentOS, it should work for most linux systems with or without slightest modifications. The process below installs Sun Java and configures Sun Java to be the default java to be used. Below are the steps I took to install and configure java in my system:
$ wget http://download.oracle.com/otn-pub/java/jdk/6u45-b15/jdk-6u45-linux-i586.tar.gz
$ tar xvfz jdk-6u45-linux-i586.tar.gz
$ echo 'export JAVA_HOME=/opt/java/jdk1.6.0_45' > /etc/profile.d/sun-jdk.sh
$ echo 'export PATH=$JAVA_HOME/bin:$PATH' >> /etc/profile.d/sun-jdk.sh
$ alternatives --install /usr/bin/java java /opt/java/jdk1.6.0_45/bin/java 2
$ java -version
java version "1.6.0_45" Java(TM) SE Runtime Environment (build 1.6.0_45-b06) Java HotSpot(TM) 64-Bit Server VM (build 20.45-b01, mixed mode)
If you wish to reconfigure the default java, you can run alternatives as below & choose the appropriate option:
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 21 June 2013
Share Local Directory With Remote Server During RDP Session
But we wish to do something extra i.e. we need to share our directory with the remote server. The good news is that the rdesktop command supports device redirection using a -r flag which can be repeated.
Your command would look something like below:
You can then access your share as a drive or media. I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 19 June 2013
Customizing Jenkins Layout
The later one does allow to add markups to the page but didn't best fit for our scenario. So we decided to use the Simple Theme Plugin. Installing the plugin is straightforward in jenkins. Once the Simple Theme Plugin is installed, a new content box will appear in your Manage Jenkins -> Configure System which will look something like below:
This plugin requires you to specify your own custom .css and .js file. The good thing about jenkins is you can place your own content at the JENKINS_INSTALL_DIR/userContent/ directory and then access it via http://yourbuildserver.tld/jenkins_path/userConent/yourfile.ext. I was working on the windows system where my jenkins install was at C:\.jenkins\ and hence I placed my CSS and image files inside the userContent directory of jenkins install folder. This should not be very difficult on any other systems if you are familiar with jenkins and your OS.
You can grab the jenkins css files from the webapp root directory (I was using tomcat so I grabbed it from inside there) and then edit the css as per your necessity. In my case, I had to change the header style only so my CSS looked something like below:
#top-panel {
background-size:100% 100%;
height: 43px;
}
#top-panel td#login-field span a {
background: none; }
#top-panel a {
background: url("title.png") 0 0 no-repeat;
display: block;
width: 107px;
height: 27px;
margin: 10px 0 -5px 0px; }
#top-panel td > a img {
display: none; }
This is all you have to do. Btw, don't fall for the readme.txt inside userContent directory which says: "Files in this directory will be served under your http://server/jenkins/userContent/". Make sure you specify the URL according to your server configuration not according to this specification thus appending "/jenkins" in your URL.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 18 June 2013
Setting Installation Of Android Application To SD Card
Follow the steps below to enable installation of new softwares to the SD card on the android phones by default (Tested on android 2.2).
- Enable USB debugging on phone (from somewhere in Settings->About Phone)
- Connect device with PC using USB cable
- Open command prompt/terminal
- Open android debugger bridge (change directory to the location where android sdk is installed)
- Type: adb.exe devices
- Type: adb.exe shell
- On the new console, type: set pmInstallLocation 2
Here, 2 means External memory
Note: "get pmInstallLocation" can be used to query for the available locations you can install softwares to.
That's all. Hope it helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 12 June 2013
Simple Pie Chart Implementation In Turbo C
This implementation makes use of pieslice() function which draws and fills the pie slice with centre x, y and radius r. The function also requires the start angle and end angle.
#include <stdio.h>
#include <conio.h>
#include <graphics.h>
#include <math.h>
#define MAX 20
#define X_CENTRE getmaxx()/2
#define Y_CENTRE getmaxy()/2
#define RADIUS 100
struct pie_data
{
char desc[100];
int freq;
int color;
int style;
float angle;
};
int main()
{
struct pie_data data[MAX];
int gd = DETECT, gm;
int i, j, k, n, total_freq = 0, start_angle = 0, end_angle = 0, xmax, ystart = 80, yend;
printf("Enter the number of items: ");
scanf("%d", &n);
for (i = 0, j = 1, k = 1; i < n; i++)
{
printf("Enter the item title: ");
scanf("%s", data[i].desc);
printf("Enter the item frequency: ");
scanf("%d", &data[i].freq);
total_freq += data[i].freq;
data[i].color = j;
data[i].style = k;
if (j++ >= 13) j = 1;
if (k++ >= 11) k = 1;
}
for (i = 0; i < n; i++)
{
float angle;
data[i].angle = 360 * (data[i].freq /(float) total_freq);
}
initgraph(&gd, &gm, "C:\\TurboC3\\BGI");
xmax = getmaxx() - 150;
setaspectratio(10000, 10000);
for (i = 0; i < n; i++)
{
end_angle = start_angle + data[i].angle;
setcolor(data[i].color);
setfillstyle(data[i].style, data[i].color);
pieslice(X_CENTRE, Y_CENTRE, (int)start_angle, (int)end_angle, RADIUS);
start_angle = end_angle;
yend = ystart + 40;
bar(xmax, ystart, xmax + 70, yend);
ystart = yend + 15;
outtextxy(xmax + 80, ystart - 20, data[i].desc);
}
getch();
closegraph();
return 0;
}
Below is the screenshot for sample run:
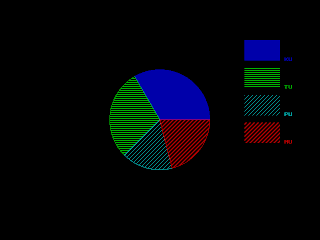
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 11 June 2013
Congratulation To SLC Graduates From Iris Academy
We would like to congratulate all the SLC appeared students and the Iris Academy and wish for the bright future ahead.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 2 April 2013
Step By Step Turbo C++ IDE In Ubuntu 12.04
First thing first, download Turbo C from internet. For your ease, I've uploaded it HERE.
We will have to install dosbox to run the windows dos mode applications so lets install it:
Once you install dosbox, unzip the content to somewhere in your $HOME directory. In my example, I unzipped the content of the Turbo C zip file into ~/Tools/TurboC3/. Now launch the dosbox by typing dosbox in the terminal. A dosbox emulation window will appear which will look like your old DOS system.
In the window, type the following (make sure you type appropriate path for your installation):
C:
cd TurboC3
INSTALL.EXE
And, then follow the on-screen information. Refer to the screenshots below:
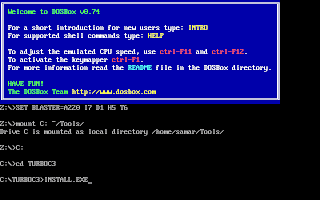
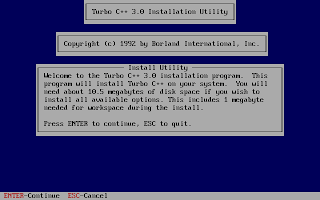
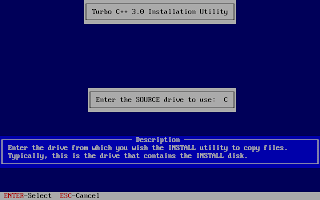
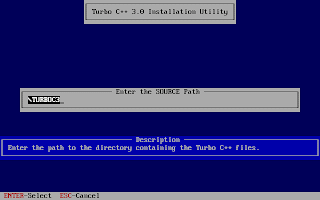
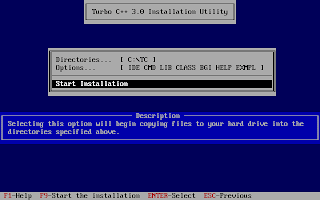
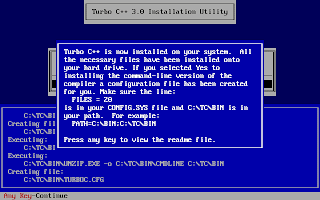
Once the installation finishes, you can then run the Turbo C by mounting the drive again and then navigation to C:\TC (cd C:\TC\BIN). If you need to use the Turbo C++ IDE frequently, my suggestion would be to add an autoexec entry in your dosbox configuration. The default configuration file resides in ~/.dosbox/dosbox-0.74.conf (My version of dosbox is 0.74 hence the file name, by default). Open up this file and in the section of [autoexec], add the lines below:
mount C: ~/Tools/
C:
cd TC\BIN
TC.EXE
Adding this entry will run the above commands during the startup of dosbox thus giving you the Turbo C IDE interface directly on running dosbox.
I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday, 31 March 2013
Simple Line Drawing In Turbo C Graphics
#include <stdio.h>
#include <conio.h>
#include <graphics.h>
int main()
{
int gd = DETECT, gm;
initgraph(&gd, &gm, "C:\\TurboC3\\BGI");
line(100, 100, 350, 100);
line(100, 100, 70, 140);
line(70, 140, 130, 140);
line(350, 100, 380, 140);
rectangle(70, 140, 130, 200);
rectangle(130, 140, 380, 200);
getch();
closegraph();
return 0;
}
I hope it proves useful for learning purpose.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Implementation Of BLA Line Drawing Algorithm
Bresenham Line Drawing Algorithm for |m| < 1
Algorithm
1) Input two points (x1, y1) & (x2, y2).
2) Determine the differences dx = x2 - x1 and dy = y2 - y1.
3) Calculate the initial decision parameter P0 = 2dy - dx.
4) For each xk along the line starting at k = 0,
if Pk < 0,
a) put a pixel at (xk + 1, yk)
b) Pk+1 = Pk + 2dy
else
a) put a pixel at (xk + 1, yk + 1)
b) Pk+1 = Pk + 2dy - 2dx.
5) Repeat step 4 for dx time.
6) End
Source Code
#include <stdio.h>
#include <conio.h>
#include <graphics.h>
#include <math.h>
int main()
{
int gd = DETECT, gm;
int x1, y1, x2, y2, dx, dy;
int x, y, i, p0, pk;
printf("Enter x1, y1: ");
scanf("%d %d", &x1, &y1);
printf("Enter x2, y2: ");
scanf("%d %d", &x2, &y2);
dx = x2 - x1;
dy = y2 - y1;
x = x1;
y = y1;
p0 = ( 2 * dy - dx);
initgraph(&gd, &gm, "C:\\TurboC3\\BGI");
pk = p0;
for (i = 0; i < abs(dx); i++)
{
if (pk < 0)
{
putpixel(x, y, WHITE);
pk += (2 * dy);
}
else
{
putpixel(x, y, WHITE);
pk += (2 * dy - 2 * dx);
}
(x1 < x2)?x++:x--;
(y1 < y2)?y++:y--;
delay(50);
}
getch();
closegraph();
return 0;
}
Make sure to provide an appropriate path for graphics library.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 26 March 2013
Implementation of DDA Line Drawing Algorithm
Digital Differential Analyzer
Algorithm
1) Input two points (x1, y1) & (x2, y2).2) Determine the differences dx = x2 - x1 and dy = y2 - y1.
3) Choose step size as the bigger value between the absolute values of dx and dy.
4) Determine x-increment = dx/step_size and y-increment = dy/step_size.
5) Start from (x0, y0) = (x1, y1).
6) For i -> 0 to stepsize:
a) draw pixel at (xi, yi)
b) set xk = xk + x-increment
b) set yk = yk + y-increment
Source Code
#include <stdio.h>
#include <conio.h>
#include <graphics.h>
#include <math.h>
int main()
{
int gd = DETECT, gm;
int x1, y1, x2, y2, dx, dy, stepsize;
float xinc, yinc, x, y;
int i;
printf("Enter x1, y1: ");
scanf("%d %d", &x1, &y1);
printf("Enter x2, y2: ");
scanf("%d %d", &x2, &y2);
dx = x2 - x1;
dy = y2 - y1;
stepsize = (abs(dx) > abs(dy))?abs(dx):abs(dy);
xinc = dx/(float)stepsize;
yinc = dy/(float)stepsize;
x = x1;
y = y1;
initgraph(&gd, &gm, "C:\\TC\\BGI");
putpixel(x, y, WHITE);
delay(10);
for (i = 0; i < stepsize; i++)
{
x += xinc;
y += yinc;
putpixel(x, y, WHITE);
delay(50);
}
getch();
closegraph();
return 0;
}
Make sure to provide an appropriate path for graphics library.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 19 March 2013
How To View Your Gmail Access History Details
In order to access the gmail history log details, you need to scroll down to the right bottom of your gmail inbox where you will notice the option to view the detail of your account which looks like below:
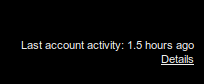
Moreover, it seems like that the details now include the user agents and/or access type information along with the IP address and time of access to the gmail account.
If you're concerned about unauthorized access to your mail, you'll be able to use the data in the 'Access type' column to find out if and when someone accessed your mail. For instance, if the column shows any POP access, but you don't use POP to collect your mail, it may be a sign that your account has been compromised.
For more information, refer to this page.
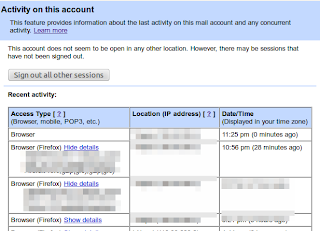
Moreover, this feature lets you log out all of your sessions other than the current session. This can come quite handy whenever you have forgotten to sign out or someone else is having an unauthorized access to your account.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 15 March 2013
Uploaded.net 48 Hours Premium Membership Coupon To Redeem
Coupon code: UBTIZYMM
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 9 March 2013
Check Battery Status From Terminal [How To]
present: yes
capacity state: ok
charging state: charged
present rate: unknown
remaining capacity: unknown
present voltage: 12276 mV
samar@Techgaun:~$ cat /proc/acpi/battery/BAT0/info
present: yes
design capacity: 4400 mAh
last full capacity: unknown
battery technology: rechargeable
design voltage: 10800 mV
design capacity warning: 250 mAh
design capacity low: 150 mAh
cycle count: 0
capacity granularity 1: 10 mAh
capacity granularity 2: 25 mAh
model number: Primary
serial number:
battery type: LION
OEM info: Hewlett-Packard
The first command provides the general status of the battery and the second command provides the detailed information about battery. The other way is to use the upower command that talks with the upowerd daemon. Upowerd daemon is a default daemon in ubuntu and few others for power statistics. Below is the command to see battery details:
native-path: /sys/devices/LNXSYSTM:00/LNXSYBUS:00/PNP0C0A:00/power_supply/BAT0
vendor: Hewlett-Packard
model: Primary
power supply: yes
updated: Sat Mar 9 10:12:17 2013 (5 seconds ago)
has history: yes
has statistics: yes
battery
present: yes
rechargeable: yes
state: empty
energy: 0 Wh
energy-empty: 0 Wh
energy-full: 47.52 Wh
energy-full-design: 47.52 Wh
energy-rate: 0 W
voltage: 12.28 V
percentage: 0%
capacity: 100%
technology: lithium-ion
If you wish to install acpi for future uses, you can do so by typing the command below:
Play around with different switches by looking over the help and man pages. You will find this tool quite useful :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 8 March 2013
Encrypt/Decrypt Confidential Data Using OpenSSL
If you wish to have full strength cryptographic functions, openssl is a perfect choice. Forget about all other tools that promise to provide high end encryption for your confidential data. Openssl is more than enough for most of your cryptographic needs. Personally, I can't just rely on some random software that promises to provide full strength cryptography but lacks documentations and detailed reviews. Openssl, however, has a well structured documentation and is an open source implementation.
Openssl supports several ciphers such as AES, Blowfish, RC5, etc., several cryptographic hash functions such as MD5, SHA512, etc., and public key cryptographies such as RSA, DSA, etc. Openssl has been widely used in several softwares most notably the OpenSSH.
Now that we know some basics about what OpenSSL is, lets move on encrypting/decrypting files/data using openssl. OpenSSL can take any file and then apply one of the cryptographic functions to encrypt the file. As an example, we encrypt a confidential file 'priv8' with a password "hello" below:
In order to decrypt the encrypted file, we can run the following command:
Now that you know the basic syntax, you can choose among several available cryptographic functions. There are several other symmetric ciphers available for use. The full list of these ciphers is provided by the command:
I hope this helps for your file encryption needs :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 7 March 2013
Make An Encrypted Call On Android Using RedPhone
RedPhone is an open source communication encryption android software that well-integrates with the system dialer and lets you use the default system dialer and contacts apps to make calls as you normally would. The tool is written by Maxie Morlinspike, the same guy who wrote a famous tool called SSLStrip for performing HTTPS stripping attacks.
Install RedPhone
It is an open source tool licensed under GPL v3; the github README says, RedPhone is an application that enables encrypted voice communication between RedPhone users. RedPhone integrates with the system dialer to provide a frictionless call experience, but uses ZRTP to setup an encrypted VoIP channel for the actual call. RedPhone was designed specifically for mobile devices, using audio codecs and buffer algorithms tuned to the characteristics of mobile networks, and using push notifications to maximally preserve your device's battery life while still remaining responsive.
If you wish to understand more on Encryption protocol, you should refer to the WIKI.
Install RedPhone
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
E-Paath - A Perfect Computer-based Learning Tool For Your Children
Developed by OLE Nepal in collaboration with the Department of Education (Nepal), this web-based software provides several modules of online lessons for classes 2-6. The software consists of 18-30 lessons organized in a weekly fashion for four subjects: Nepali, English, Mathematics, and Science. The contents for science are available in both English and Nepali languages. However, mathematics is available only in Nepali language.
E-paath is a flash based content and hence requires flash player and can be run through any of the major web browsers such as Mozilla Firefox, Google Chrome, etc. Since e-paath is a web based content, you can run it in any platform without any problem (I had to change a little bit of code in karma.html file to run the tool smoothly in Linux but its still fine; having a web server to serve the pages solves all errors though).
You can download e-paath from HERE. For installation help, you can refer to this page. You can also access the software online from HERE. Btw, there is no specifically linux version of tool available in the website (except for Sugar desktop environment) and don't try to mirror the online version of e-paath as flash contents seem to be internally referencing the configuration files. Your best bet is to download either of the two available versions and then delete all the unnecessary stuffs in there. It just runs fine.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 12 February 2013
Chaining The Proxies With ProxyChains
ProxyChains is a tool for tunneling TCP and DNS traffics through chain of several proxy servers which supports HTTP, SOCKS4, and SOCKS5 proxy servers. Hence, this tool leverages several usages such as anonymity, bypassing filters, running any program through proxy servers, etc.
You can DOWNLOAD proxychains from SourceForge. In ubuntu, you can directly install it from repos:
Once you have installed the proxychains, you need to configure this tool. The global configuration file is located at /etc/proxychains.conf so if you wish to have your own configuration file, you could either create the proxychains.conf file in the current working directory or at $HOME/.proxychains/proxychains.conf.
In my example, I'll edit the global configuration file by issuing the command:
First, we will have to select the kind of chaining option we want to use. We can use one of the dynamic_chain, strict_chain, and random_chain chaining options. In most cases, it is good to just use the dynamic_chain so we uncomment the line containing dynamic_chain and comment all other chaining options.
Then we need to grab some proxies and then insert at the end of our configuration file which would look like:
socks5 192.168.2.90 3128
socks5 1**.1**.*.* 8080
You could add as much as proxy servers in the list. Btw, the asterisks in the above example do not mean wildcards, they are just there to symbolize some proxy server. There are free sites on the Internet which provide big database of different kinds of proxies. Even several proxy scrapers are available all over the internet and you could even write one on your own. So getting list of good proxies is not the difficult job. Once you finish the configuration, you can run any command through proxychains. The syntax is as simple as below:
For example, below is the example nmap scan run through the proxychains:
P.S. If you are interested in some GUI for using proxychains, you can use ProxyChainsGUI. Lastly, the default package from Ubuntu repository seems to be missing the proxyresolv command so I would recommend to compile the source code locally.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 7 February 2013
NCell Paisa Double For Prepaid and Pro Classic customers
With the Ncell's Paisa Double offer, you will be able to double the said amount. Ncell says that it is a new offer that acknowledges the loyalty of Ncell customers by providing them various amounts to double.
Once you have enough main balance, you can activate the offer by dialing 1212. In order to utilize the scheme, you have to follow the steps as below:
- Dial 1212 and listen to find out what amount you can double. Then press 1 to get the double of the said amount. Alternatively, you can also dial *1212# and press 1.
- After you press 1, the said amount will be deducted from your main balance and the double of it will be added as your Paisa Double balance.
While the offer sounds great, it is only applicable within Ncell network. You can use the Paisa Double balance to make calls, send SMS and MMS within Ncell network and even to access internet. You can subscribe Ncell Paisa Double offer only once and it will be auto-renewed every week until you deactivate or till the offer ends.
Dial *101# to know your remaining Paisa Double balance. If you wish to deactivate the service, type R and send it to 1212 through SMS. However, you can again activate if you wish within the offer period.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday, 30 January 2013
Search Text Over Multiple PDF Files In Linux
The pdfgrep tool lets you perform grep style search over multiple pdf files easily from the terminal. It depends upon the poppler package and under ubuntu, you can just type the command below to install pdfgrep.
Once pdfgrep is installed, you can perform any kind of search like you would do while using the grep command. Enjoy grepping the PDF files :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 29 January 2013
Turn Your Greasemonkey Script Into Firefox Extension
Greasemonkey Compiler
I hope the URL proves useful to you guys :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Swasthani.com Swasthani Ripper
From the site itself, Sri Swasthani Brata Katha is a very popular ritual observed in Nepal in the Poush month (January – February) during winter. Goddess Sri Swasthani, known to grant wishes of her devotees, is worshipped for the whole month of Poush. The Swasthani Brat Katha (story) is recited everyday. The month long telling of the tales are dedicated to the Goddess and the stories that are mainly narrated are those of Swasthani Devi, Lord Shiva and other Gods.
#!/bin/bash ############################################### # Swasthani.com Swasthani Ripper # # Samar @ http://www.techgaun.com # ############################################### if [[ ! -f /tmp/swasthani.txt ]] then wget http://www.swasthani.com/ -O - | egrep '<li class="leaf( first| last)?"><a href="/swasthani/' | grep -o '<a .*href=.*>' | sed -e 's/<a /\n<a /g' | sed -e 's/<a .*href=['"'"'"]//' -e 's/["'"'"'].*$//' -e '/^$/ d' > /tmp/swasthani.txt fi while read -r line do wget "http://www.swasthani.com$line" -O - | egrep 'data="soundFile=http://www.swasthani.com/system/files/' | cut -d\" -f6 | cut -d= -f2 | wget -nc -i - done </tmp/swasthani.txt
Save the above file as swasthani, then chmod for executable permission and run it. If you have problem copying above code, you can check the Swasthani Downloader at GitHub. Enjoy listening Swasthani, geeks :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
How To Check Which Groups You Belong To
From the man page, the groups command does is:
Print group memberships for each USERNAME or, if no USERNAME is specified, for the current process (which may differ if the groups database has changed).
So if you are interested in finding what group a particular user is in, run the command as below. Replace samar with your USERNAME and you are good to go:
samar : samar adm cdrom sudo vboxusers ....
I hope this proves useful :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday, 26 January 2013
NCell PRBT Settings Information
Original Link: PRBT Information @ Ncell
Q1.What is PRBT?
PRBT service enables the ones who call you to listen to a popular melody or sound instead of the regular tone. The sound or melody is heard by the caller till the call is answered. Your friends and partners, regardless of operator, location and phone model while calling you can hear melodies, sounds and personal greetings chosen by you instead of usual phone tone.
Q2. How to activate PRBT service?
PRBT can be activated by one of the following ways:
I. SMS: On your Message box type A and send it to 900227
II. IVR: Dial 9208 and follow the instruction.
III. USSD: Dial *100*2# and follow the USSD guide instruction.
Q3. How to set a PRBT?
Any PRBT of your choice can be set via SMS, IVR or Web once the user has activated the PRBT service. Stated below are the ways a subscriber can set a PRBT.
I. SMS: Type BUY
II. Web :
i. Log on to prbt.ncell.com.np
ii. Click on Order for your choice of PRBT song
III. IVR: Dial 9208 to choose the tone of your choice.
Q4. What are the features with new PRBT system?
The PRBT system allows a subscriber to perform the following:
I. SMS
a. Download multiple PRBTs at once
Example:
Down
b. Gift PRBT to friend
Example: Gift
II. Web
To activate any of the features below, the user will have to login with mobile number and password on prbt.ncell.com.np
a. Assign different PRBT to different callers.
i. Click on MY PRBT > PRBT Settings > Advanced Setting
b. Create Group and allocate a PRBT for a group.
i. Click on MY PRBT > Group Management
c. Play different PRBT in different time slots.
i. Click On MY PRBT > PRBT setting > Add
d. Copy a PRBT from a friend.
i. Click on MY PRBT > Copy PRBT
Q5. How much does a PRBT cost and what is the validity?
Each PRBT will attract Rs. 10 excluding the taxes.
Q6. Is there monthly subscription price?
Yes. There will be Rs 10 monthly subscription price without applicable taxes. The subscription will be renewed automatically unless the subscriber chooses to discontinue the service.
Q7. How deactivate PRBT?
You can deactivate by any of the following ways:
I. SMS : In your message box type R and send it to 900227
II. IVR : Dial 900 follow instruction
III. USSD : Dial *100*2# and follow the instruction
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subterfuge - An Automated MITM Attack Framework
Subterfuge largely transforms the complexity of performing the man-in-the-middle attacks with the tools such as ettercap and makes it far more easier to launch various form of MITMs. Hence, even a general computer user can perform MITM using this tool. Subterfuge provides a very clear interface accessible over HTTP through browser through which we can view the intercepted authentication data. The tool also supports several other form of MITM attacks such as session injection, http code injection, fake AP, and DNS spoofing.
Currently, the 4.3 beta version of this tool is available as the latest release. You can download the tool and read about the tool at code.google.com/p/subterfuge.
Installation is straightforward. Download the tar file from the above link and then run the following commands in terminal:
After a while, the installation will complete. Now you can run the subterfuge framework by typing subterfuge in your terminal. Enjoy hacking :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 22 January 2013
Simple Sorting Algorithm Using DMA
#include <stdio.h>
#include <stdlib.h>
int main()
{
int *arr, i, j, n;
printf("Enter the number of items: ");
scanf("%d", &n);
arr = malloc(n * sizeof(int));
for (i = 0; i < n; i++)
{
printf("Enter the %dth item: ", i + 1);
scanf("%d", &arr[i]);
}
for (i = 0; i < n - 1; i++)
{
for (j = 0; j < n - 1; j++)
{
int temp;
if (arr[j] > arr[j + 1])
{
temp = arr[j];
arr[j] = arr[j + 1];
arr[j + 1] = temp;
}
}
}
printf("The sorted array is:\n");
for (i = 0; i < n; i++)
{
printf("%d\n", arr[i]);
}
return 0;
}
samar@samar-Techgaun:~$ gcc -Wall -o sort sort.c samar@samar-Techgaun:~$ ./sort Enter the number of items: 5 Enter the 1th item: 2 Enter the 2th item: 4 Enter the 3th item: 1 Enter the 4th item: 92 Enter the 5th item: 45 The sorted array is: 1 2 4 45 92
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Matrix Multiplication Using DMA [C Source Code]
#include <stdio.h>
#include <stdlib.h>
int main()
{
int **A, **B, **C, m, n, p, q, i, j, k;
printf("Enter the size of matrix A: ");
scanf("%d %d", &m, &n);
printf("Enter the size of matrix B: ");
scanf("%d %d", &p, &q);
if (n == p)
{
A = malloc(m * sizeof(int));
B = malloc(p * sizeof(int));
C = malloc(m * sizeof(int));
for (i = 0; i < m; i++)
{
A[i] = malloc(n * sizeof(int));
C[i] = malloc(q * sizeof(int));
}
for (i = 0; i < p; i++)
{
B[i] = malloc(q * sizeof(int));
}
printf("Enter the matrix A:\n\n");
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
scanf("%d", &A[i][j]);
}
}
printf("Enter the matrix B:\n\n");
for (i = 0; i < p; i++)
{
for (j = 0; j < q; j++)
{
scanf("%d", &B[i][j]);
}
}
for (i = 0; i < m; i++)
{
for (j = 0; j < q; j++)
{
C[i][j] = 0;
for (k = 0; k < n; k++)
{
C[i][j] = C[i][j] + (A[i][k] * B[k][j]);
}
}
}
printf("Multiplication of given matrices is: \n\n");
for (i = 0; i < m; i++)
{
for (j = 0; j < q; j++)
{
printf("%d ", C[i][j]);
}
printf("\n");
}
for (i = 0; i < m; i++)
{
free(A[i]);
free(C[i]);
}
for (i = 0; i < p; i++)
{
free(B[i]);
}
free(A);
free(B);
free(C);
}
else
{
printf("Matrix multiplication is not possible for given size\n\n");
}
return 0;
}
samar@samar-Techgaun:~$ gcc -Wall -o matrix_mul matrix_mul.c samar@samar-Techgaun:~$ ./matrix_mul Enter the size of matrix A: 3 2 Enter the size of matrix B: 2 3 Enter the matrix A: 1 2 3 4 5 6 Enter the matrix B: 1 2 3 4 5 6 Multiplication of given matrices is: 9 12 15 19 26 33 29 40 51
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 17 January 2013
Addition Of Two Matrices Using DMA [C Source Code]
#include <stdio.h>
#include <stdlib.h>
int main()
{
int **A, **B, **C, m, n, p, q, i, j;
printf("Enter the size of matrix A: ");
scanf("%d %d", &m, &n);
printf("Enter the size of matrix B: ");
scanf("%d %d", &p, &q);
if (m == p && n == q)
{
A = malloc(m * sizeof(int));
B = malloc(m * sizeof(int));
C = malloc(m * sizeof(int));
for (i = 0; i < m; i++)
{
A[i] = malloc(n * sizeof(int));
B[i] = malloc(n * sizeof(int));
C[i] = malloc(n * sizeof(int));
}
printf("Enter the matrix A:\n\n");
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
scanf("%d", &A[i][j]);
}
}
printf("Enter the matrix B:\n\n");
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
scanf("%d", &B[i][j]);
}
}
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
C[i][j] = A[i][j] + B[i][j];
}
}
printf("The addition of two matrices is: \n\n");
for (i = 0; i < n; i++)
{
for (j = 0; j < m; j++)
{
printf("%d ", C[i][j]);
}
printf("\n");
}
for (i = 0; i < m; i++)
{
free(A[i]);
free(B[i]);
free(C[i]);
}
free(A);
free(B);
free(C);
}
else
{
printf("Matrix addition is not possible for given size\n\n");
}
return 0;
}
Below is a sample run along with the compilation step.
samar@samar-Techgaun:~$ gcc -Wall -o matrix_addn matrix_addn.c samar@samar-Techgaun:~$ ./matrix_addn Enter the size of matrix A: 2 2 Enter the size of matrix B: 2 2 Enter the matrix A: 1 2 3 4 Enter the matrix B: 4 3 2 1 The addition of two matrices is: 5 5 5 5
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday, 15 January 2013
Transpose Of Matrix Using DMA [C Source Code]
Below is the source code:
#include <stdio.h>
#include <stdlib.h>
int main()
{
int **matrix, **transpose, m, n, i, j;
printf("Enter the size of matrix: ");
scanf("%d %d", &m, &n);
matrix = malloc(m * sizeof(int));
transpose = malloc(n * sizeof(int));
for (i = 0; i < m; i++)
{
matrix[i] = malloc(n * sizeof(int));
}
for (i = 0; i < n; i++)
{
transpose[i] = malloc(m * sizeof(int));
}
printf("Enter the matrix:nn");
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
scanf("%d", &matrix[i][j]);
}
}
for (i = 0; i < m; i++)
{
for (j = 0; j < n; j++)
{
transpose[j][i] = matrix[i][j];
}
}
printf("The transpose of given matrix is: nn");
for (i = 0; i < n; i++)
{
for (j = 0; j < m; j++)
{
printf("%d ", transpose[i][j]);
}
printf("n");
}
for (i = 0; i < m; i++)
{
free(matrix[i]);
}
for (i = 0; i < n; i++)
{
free(transpose[i]);
}
free(matrix);
free(transpose);
return 0;
}
Below is the sample run:
samar@Techgaun:~$ gcc -Wall -o transpose transpose.c samar@Techgaun:~$ ./transpose Enter the size of matrix: 2 3 Enter the matrix: 1 2 3 4 5 6 The transpose of given matrix is: 1 4 2 5 3 6
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday, 11 January 2013
Java 0-day In The Wild - Disable Java Plugin NOW
French researcher Kaffeine discovered that the java 0-day has been spotted to be making big hits daily, in a blog post. This particular exploit has proven to be very serious threat for the users. The folks at AlienVault Lab have also reproduced the exploit and it seems to work over all the java versions across all platforms which is a very serious threat.
As for now, the users are highly urged to disable their JAVA plugins right now so that they do not get hit by these 0-days.
So what are you waiting for?
Important links:
How To Disable Java Plugin
Kaffeine's blog post
Alien Vault Labs Post
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday, 10 January 2013
Create Backup Of List Of Apps Installed In Ubuntu
Now the list of packages will be saved in the installed_apps file and you can use it for future reference. I hope this is useful ;)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
